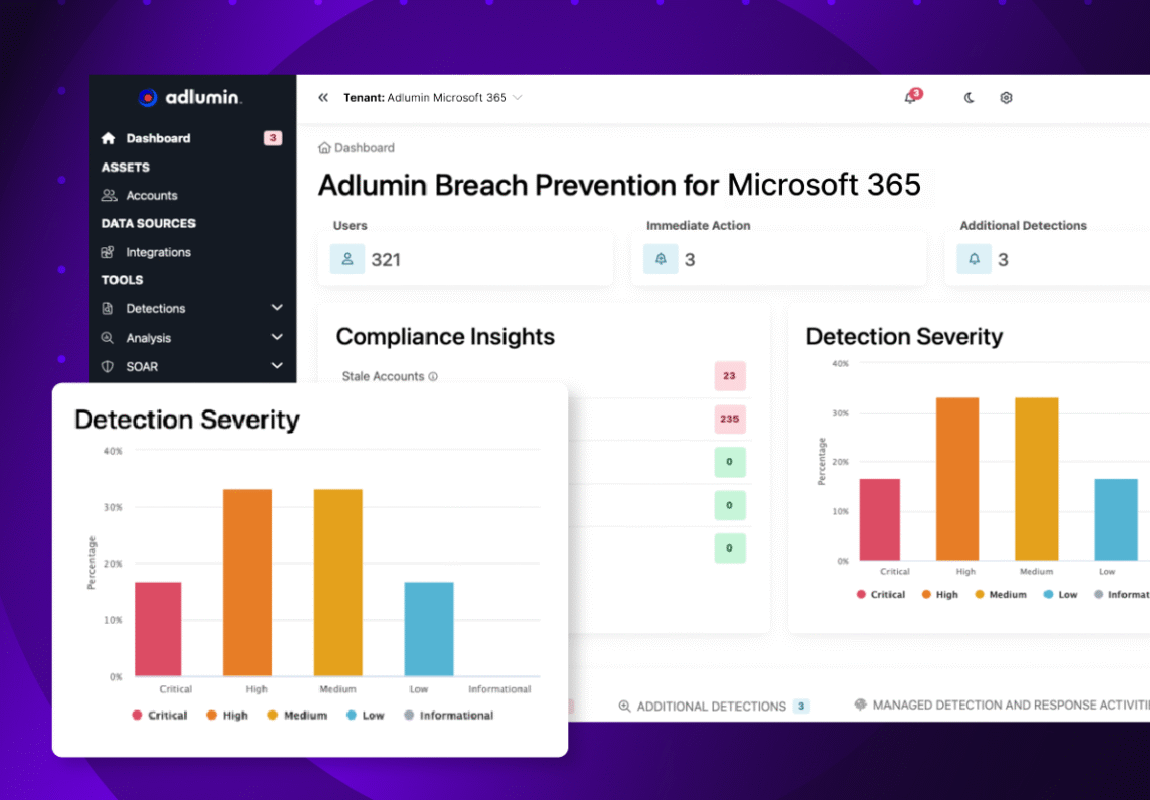
Breach Prevention for Microsoft 365 Detect and stop identity attacks

Cybercriminals are shifting their focus from traditional endpoints to cloud identities, gaining more access and moving completely undetected across Microsoft 365. Detect these user behaviors early to stop threats before they escalate.
24/7 protection for Microsoft 365 users
Adlumin provides continuous identity protection through its XDR platform, ingesting Microsoft 365 telemetry and using machine learning to build behavioral baselines. When activity deviates, our intelligent engine automatically neutralizes threats based on severity. You get expert-driven detection and response, powered by advanced analytics—without the operational burden.
Sit back, relax, and stay ahead of attacks
Adlumin Breach Prevention helps you protect your most vulnerable assets without your security team having to work overtime. And with our intelligent detection and automated response capabilities, you can stay ahead of attacks, keeping your Microsoft environment secure from the get go.

Phishing is the leading cause of 90% of data breaches.
Credential phishing accounted for 91% of active threat reports, Security Magazine, April 2024.
Stolen credentials were the most commonly used data in breaches.
Verizon Data Breach Investigations Report 2023
60% of organizations were compromised last year by an attack involving a compromised credential.
Proofpoint, State of the Phish 2024
29% of organizations face weekly credential phishing attempts.
Verizon Data Breach Investigations Report 2023
The vast majority of breaches today involve the human element – whether it’s stolen credentials, privilege misuse, or simple human error.
Microsoft Digital Defense Report 2023
Managed Detection and Response packages
| Microsoft 365 Breach | MDR Standard | MDR Advanced | |
|---|---|---|---|
| Data | |||
| Data Retention | 30 days | 30 days | 90 days |
| Sources | |||
| Adlumin Endpoint Agent | - | ||
| API Integrations | Microsoft 365 only | ||
| Adlumin VM Collector for non-API Data Ingestion (ex. Syslog) |
- | - | |
| Capabilities | |||
| Darknet Monitoring* | - | ||
| Cyber Threat Intelligence | |||
| SIEM | Limited to Microsoft data | ||
| Vulnerability Scanning | - | ||
| Network Insights | - | ||
| Reporting and Compliance | |||
| UEBA | |||
| Honeypots | - | - | |
| SOAR | Identity only |
* Darknet Monitoring not applicable for educational institutions
