5 Steps to getting started with Zero Trust

In the previous two blogs, we’ve traced the outline of Zero Trust from philosophy and principles to frameworks and marketing terms. In this blog Pete Roythorne talked to Marc Barry, Co-Founder and Chief Product Officer at Enclave, about how you can get started with Zero Trust Network Access.
You can read the previous blogs here:
- Demystifying Zero Trust: Why MSPs Need to Take it Seriously
- Demystifying Zero Trust: Understanding the Zero Trust Security Model
To do this we’re going to use CISA’s Zero Trust Maturity Model as a baseline for understanding. While it’s only one of many paths available to support the transition to Zero Trust, it’s particularly useful for small and mid-size organizations precisely because the authors recognize the need to approach Zero Trust as a journey. CISA’s model is broken down into five key pillars:
- User Identity: The ability to uniquely describe a user or resource.
- Devices: Any asset (including hardware, software, firmware, servers, desktop and laptop machines, printers, mobile phones, IoT devices, networking equipment etc.) that can connect to a network.
- Networks: Internal networks, wireless and on-premise, Cloud, home workers, B2B partnerships.
- Applications and Workloads: Programs, services and workloads that execute on-premises, on mobile devices, and in cloud environments.
- Data: All structured and unstructured files and fragments that reside or have resided in systems, devices, networks, applications, databases, infrastructure, and backups (including on-premises and virtual environments) as well as the associated metadata.
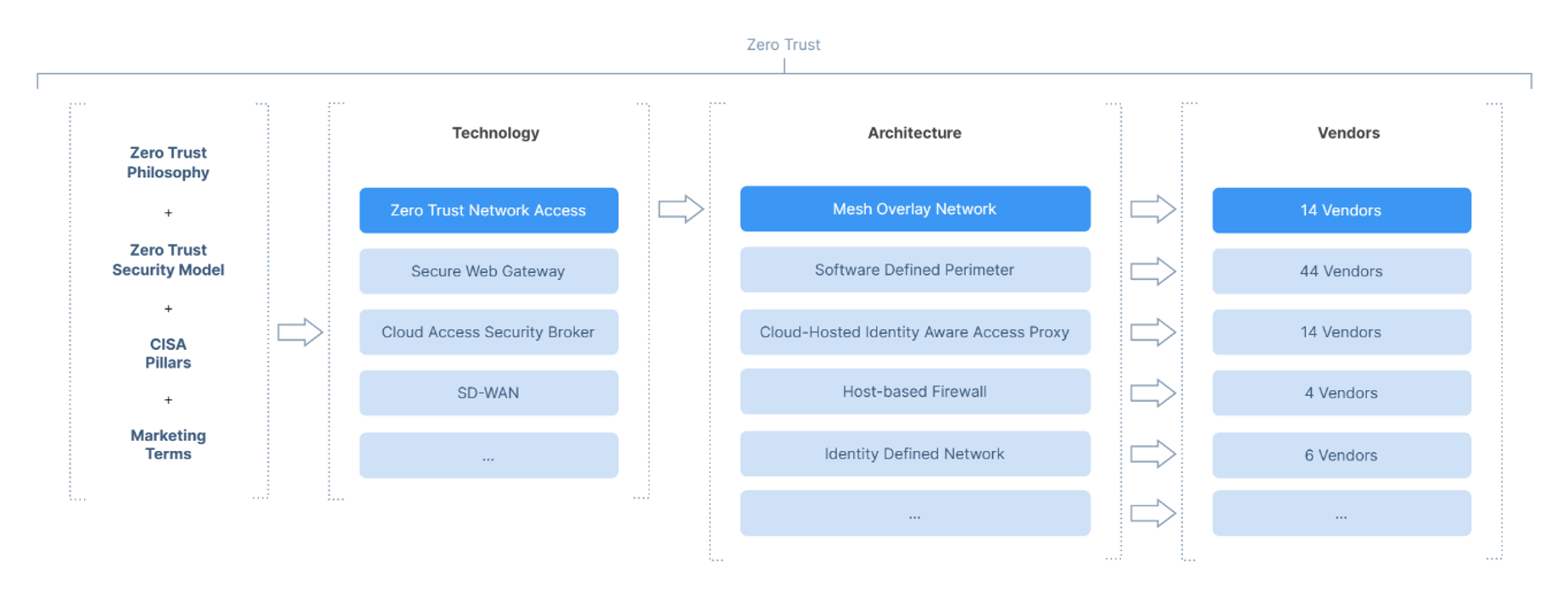
The below list demonstrates how each pillar can be serviced by one or more core technologies:
- Secure Web Gateway (SWG): Filtering unwanted ads/malware and other threats from user-initiated web/internet traffic.
- Cloud Access Security Broker: Intermediary service deployed between users and cloud service providers ensure compliance, visibility and data security.
- Zero Trust Network Access: Corporate VPN replacement. Secure access to applications and services based on identity verification, without relying on traditional network-based perimeter security.
- SD-WAN: Manages and optimizes network traffic across wide area networks (WAN) links to automatically determine the most effective way to route traffic to and from branch offices and data centers.
The below chart, shows how each technology in turn can be implemented using one of several architectural approaches. For example, one vendor may decide to deliver their solution entirely via the Cloud, another may elect to build appliances for the MSP to deploy into the customer’s network.
Getting started with Zero Trust
As an MSP, getting started with Zero Trust is an exercise in the art of right-sizing both effort and tooling, but you might be surprised by how much you already have in place. Here’s a five-step process to help you start your Zero Trust journey.
Step 1: Identity
Deploy an Identity Provider (IdP) into your customer’s organization. This is the foundation of any Zero Trust journey and must be your first step. Consider Microsoft’s Entra ID, Okta, Duo or many others. If your customer is using on-premise Active Directory, now is the time to synchronise user identities between local and cloud directories with Azure AD Connect. Remember: One user, one login, and one Identity Provider.
- Establish and manage corporate identities with a single Identity Provider.
- Enforce Multi-Factor Authentication (MFA) across all applications.
Step 2: Devices
Devices may be company-owned, bring-your-own-device (BYOD) property of employees, or owned by partners/visitors.
Start with company-owned devices registered in your RMM.
- Create an inventory of all corporate devices using your RMM platform.
- Implement endpoint management across all corporate devices.
- Safeguard these devices from threats by applying Endpoint Detection and Response (EDR) or Endpoint Protection Platform (EPP).
Step 3: Networks
Your focus here is to create a secure foundation for your customer to do business. Think about network access and the types of traffic patterns your customer needs. Does the customer require private access to on-premise, cloud or partner resources (such as privately addressable devices, non-browser apps, SSH, RDP, SMB, thick clients)? If so, consider deploying a ZTNA solution.
What about private access to trusted SaaS applications, is access to SaaS applications locked down to prevent unauthorised login attempts? If not, consider again deploying ZTNA, or use a cloud access security broker (CASB) solution if your customer needs more control over access and auditing.
- Employ DNS filtering or Secure Web Gateways (SWGs) with SSL/TLS inspection to block harmful Internet-based threats.
- Deploy ZTNA or CASB according to your customer’s traffic patterns.
- Segment each user’s network access to control and restrict internal movement.
- Close all inbound ports that are open to either the Internet or LAN for application delivery.
- Integrate any tooling you deploy with your RMM and IdP solutions.
- Ensure company data is encrypted when in motion.
- If there’s a VPN server, replace it.
For the purposes of this guide, we’ve assumed that as an MSP you’re not intentionally managing publicly addressable applications beyond static brochureware websites for your customer. Removing implicit trust from software development and deployment pipelines introduces many more touch points for Zero Trust principles, complicates the customer’s journey beyond the scope of this guide.
Step 4: Applications
- Enable DMARC, DKIM, and SPF on customer domain names.
- Monitor inbound emails and filter out phishing attempts.
- Inventory all corporate applications and ensure appropriate access controls are enforced with ZTNA and IdP integration.
Step 5: Data
- Ensure data-at-rest is encrypted on all devices using whole disk encryption (available in all modern operating systems).
- Ensure access to data is appropriately user-permissioned and all access is recorded.
- Consider whether your customer requires ransomware protection, it may be part of your EDR or EPP solution.
What’s next?
Create a Zero Trust dialogue with your customers.
After setting up the initial technologies for Zero Trust, consider the scale of deployment, automation level, and the unique context of each customer. This foundational phase can be just the beginning. The direction to take next should be shaped by discussions specific to each customer’s risk profile, their willingness to invest further, potential benefits, and cost considerations.
Here are two stages to follow up the five steps above.
1. Maintain a steady state
After implementing the initial technologies, your goal might simply be to enter a “steady state” with each customer. The key is to recognize that like anything else, over-investing can lead to diminishing returns and create fatigue. Your customer might feel that their Zero Trust journey is as mature as it needs to be.
At this stage, you’ve tailored the Zero Trust approach to suit their immediate requirements, which allows you to transition into a steady-state mode of operation for the customer.
During a steady-state phase, your role could involve providing ongoing management, optimizing how visibility and analytics capabilities are used with continuous monitoring to analyse logs and events in order to enforce policy and automate security responses. Steady state also provides an opportunity to streamline your own management of the customer’s environment through automations. This can reduce time demands and increase the efficiency in your own service desk operations.
Quarterly Business Reviews are a great time to discuss the value that your solution brings your customers and ideally where you’re jointly reassessing whether the current level of Zero Trust maturity is still appropriate as their businesses grows and adapts to new challenges and security risks.
2. Grow your customer’s Zero Trust capabilities
Explore your customers’ aspirations and use the CISA maturity model to help them understand not only what’s been achieved, but also what’s possible, and how it aligns with their security goals.
For example, is your customer using phishing-resistant MFA—like FIDO2 or PIV? Is Identity and Network tooling integrated—identifying risk in real-time and dynamically adjusting access? How narrow is the scope of each granted access? Is data loss prevention relevant to you customer?
Questions to ask ZTNA vendors
Finally, when you’re ready to take the plunge with a ZTNA vendor, here’s a list of questions you should ask them.
- Coverage and Scalability: “Does your product provide comprehensive coverage for all types of network traffic (North-South and East-West)? How will it adapt to our range of customer needs and future expansions?”
- IP Address Change Management: “In case of an IP address alteration in workloads, what is the required management overhead?”
- Onboarding Process for New Sites: “What is the process for integrating a new site or location? Please detail the deployment requirements, lead times, management involvement, and costs.”
- Business Model Alignment: “Does your business model align with our operational structure as an MSP, particularly regarding pricing models, bulk purchasing requirements and sector discounts? Do you offer Not-for-Resale licenses for internal deployment and testing purposes?”
- Technical Support Responsiveness: “Can you describe the responsiveness and availability of your technical support, including the use of platforms like Slack or Discord for real-time assistance?”
- Integration with RMM and PSA Tools: “How does your product integrate with existing Remote Monitoring and Management (RMM) and Professional Services Automation (PSA) tools?”
- Incremental Deployment Capability: “Is it possible to implement your solution incrementally across our network? Does it require rip-and-replace or can it co-exist with current technologies? Does the MSP need to deploy hardware or appliances into the customer environment?”
- Trial Period Availability: “Do you offer a trial period for your product to assess its suitability for our needs?”
- Usage Limitations: “Are there any scenarios or environments where your product cannot be deployed or may not function optimally?”
- Acknowledgment of Solution Limitations: “What do you consider to be the weakest aspect of your solution, and how open are you to feedback and improvements in these areas?”
- Transparency in Platform Uptime: “Do you publicly disclose your platform’s uptime statistics and availability in real-time? If not, can you explain why?”
The team at Enclave Networks provides a solution based on a “Mesh Overlay Network”, but we also maintain a curated, impartial and open-source directory of ZTNA vendors and architectures so that the community as a whole can benefit from honest, impartial, and open knowledge—this tracks about 90 different vendors at the time of writing.
The directory can be found at: https://zerotrustnetworkaccess.info/
 |
Enclave has developed and maintains integrations with N‑sight and N‑central, via close collaboration with N‑able’s Technology Alliance Program. You can find out more about TAP by visting www.n-able.com/partnerships/technology-alliance-program.
To see all the industry-leading integrations provided by our TAP Partners visit www.n-able.com/integrations |
© N‑able Solutions ULC e N‑able Technologies Ltd. Tutti i diritti riservati.
Il presente documento viene fornito per puro scopo informativo e i suoi contenuti non vanno considerati come una consulenza legale. N‑able non rilascia alcuna garanzia, esplicita o implicita, né si assume alcuna responsabilità legale per quanto riguarda l’accuratezza, la completezza o l’utilità delle informazioni qui contenute.
N-ABLE, N-CENTRAL e gli altri marchi e loghi di N‑able sono di esclusiva proprietà di N‑able Solutions ULC e N‑able Technologies Ltd. e potrebbero essere marchi di common law, marchi registrati o in attesa di registrazione presso l’Ufficio marchi e brevetti degli Stati Uniti e di altri paesi. Tutti gli altri marchi menzionati qui sono utilizzati esclusivamente a scopi identificativi e sono marchi (o potrebbero essere marchi registrati) delle rispettive aziende.

