Threat Hunting Explained: See It in Action, Learn How It Works
Most IT and security professionals have heard of threat hunting – but few have seen it in action or fully understand how it works in the real world. That’s about to change.
In this on demand webinar, Jim Waggoner and Kevin O’Connor guide you through a hands-on threat hunting session, showing how they identify, investigate, and surface hidden threats across cloud and endpoint environments.
You’ll learn:
- What threat hunting actually is (and how it differs from investigation)
- How to uncover threats hiding in normal traffic
- Why correlation across identity and endpoint data matters
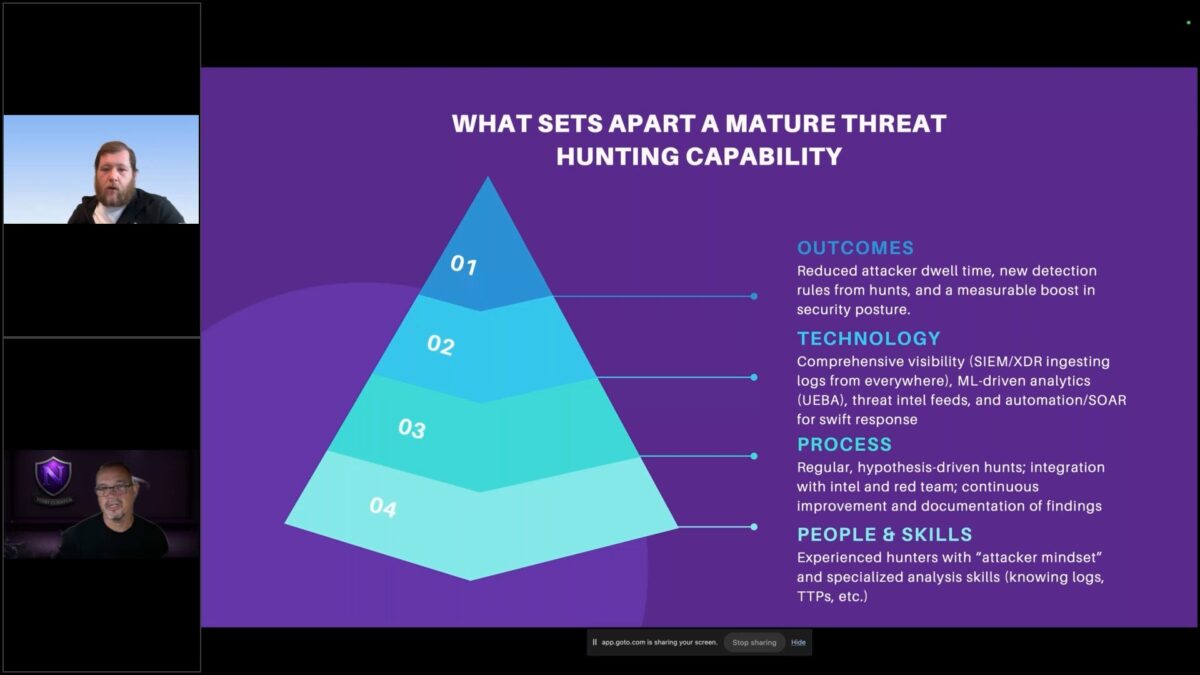
- What sets apart a mature, effective threat hunting capability