2025 Annual Threat Report
SMBs in the crosshairs

SMBs are now prime targets for sophisticated cybercriminals
Identity is the new SMB perimeter
Digital identities, and not IP addresses, now mark the front line of attack for SMBs.
Over the past 18 months, credential abuse featured in nine out of every 10 confirmed web application breaches—and compromised credentials remain the single fastest path into an organization’s data and cloud workloads.1

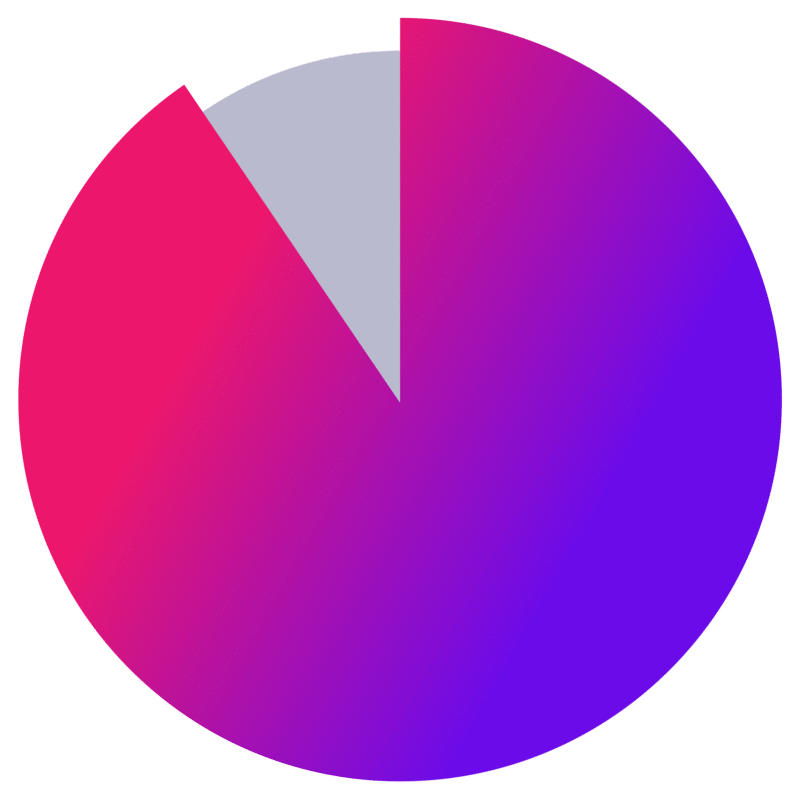
88% of confirmed SMB breaches involve ransomware or data extortion*
*Verizon 2025 Data Breach Investigations report3
Threats that routinely burn SMBs

Business email compromise (BEC)
Business email compromise (BEC)
The FBI received 21,489 BEC complaints in 2023, with adjusted losses exceeding USD 2.9 billion.2 Verizon’s 2025 Data Breach Investigations Report (DBIR) shows BEC now rivals ransomware as the top incident pattern for organizations under 1,000 employees.3

Ransomware‑as‑a‑Service (RaaS)
Ransomware‑as‑a‑Service (RaaS)
Affiliate programs such as LockBit, BlackCat/ ALPHV, and Play lower the barrier to entry. Recent CISA #StopRansomware advisories detail Play attacks through exposed RDP and unpatched VPNs, and LockBit’s exploitation of Citrix Bleed (CVE-2023-4966) against healthcare and professional services firms.4 ENISA tracks ransomware as the top EU threat for 2023, noting increased multiple-extortion tactics and shrinking dwell times.5 Regular offline backups, hardened remote access, patch management, and EDR coverage remain the best defense.

Credential stuffing and MFA fatigue
Credential stuffing and MFA fatigue
Cloud adoption puts reused passwords in adversaries’ crosshairs. CISA warns that push-notification “MFA bombing” and SMS interception can bypass weak factors; it urges a migration to phishing-resistant FIDO/WebAuthn or passkeys.6 The Verizon 2025 DBIR attributes over 60% of web-app breaches to stolen credentials or brute-force attacks, underscoring passwordless initiatives as a higher-ROI investment than post-quantum pilots.7

Stay a step ahead with the 2025 Annual Threat Report

[1] https://www.reuters.com/world/us/complaints-about-ransomware-attacks-us-infrastructure-rise-9-fbi-says-2025-04-23/
[2] https://www.enisa.europa.eu/sites/default/files/publications/ENISA%20Threat%20Landscape%202023.pdf
[3] https://www.ic3.gov/annualreport/reports/2023_ic3report.pdf
[4] https://www.verizon.com/business/resources/Tea/reports/2025-dbir-data-breach-investigations-report.pdf
[5] https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-325a
[6] https://www.enisa.europa.eu/sites/default/files/2024-11/ENISA%20Threat%20Landscape%202024_0.pdf
[7] https://www.cisa.gov/sites/default/files/2023-01/fact-sheet-implementing-phishing-resistant-mfa-508c.pdf

