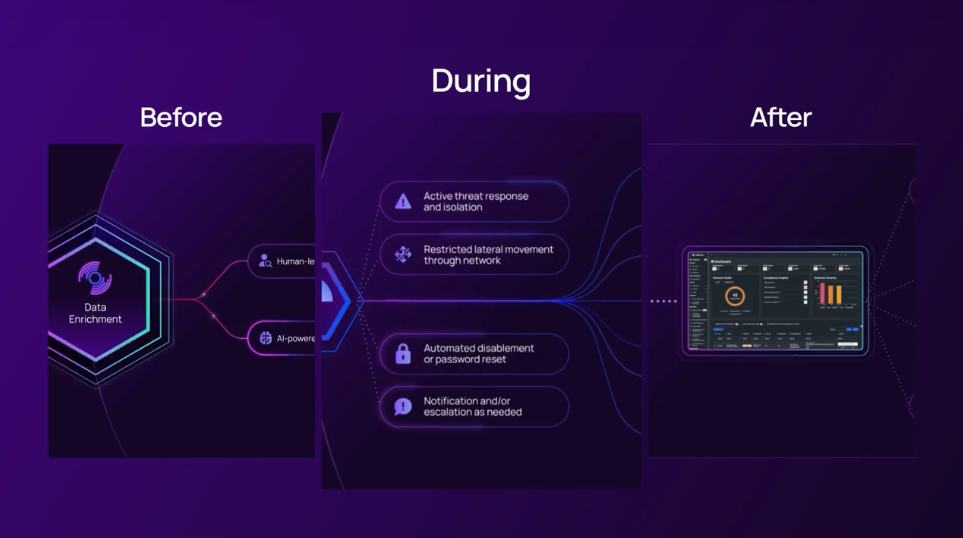
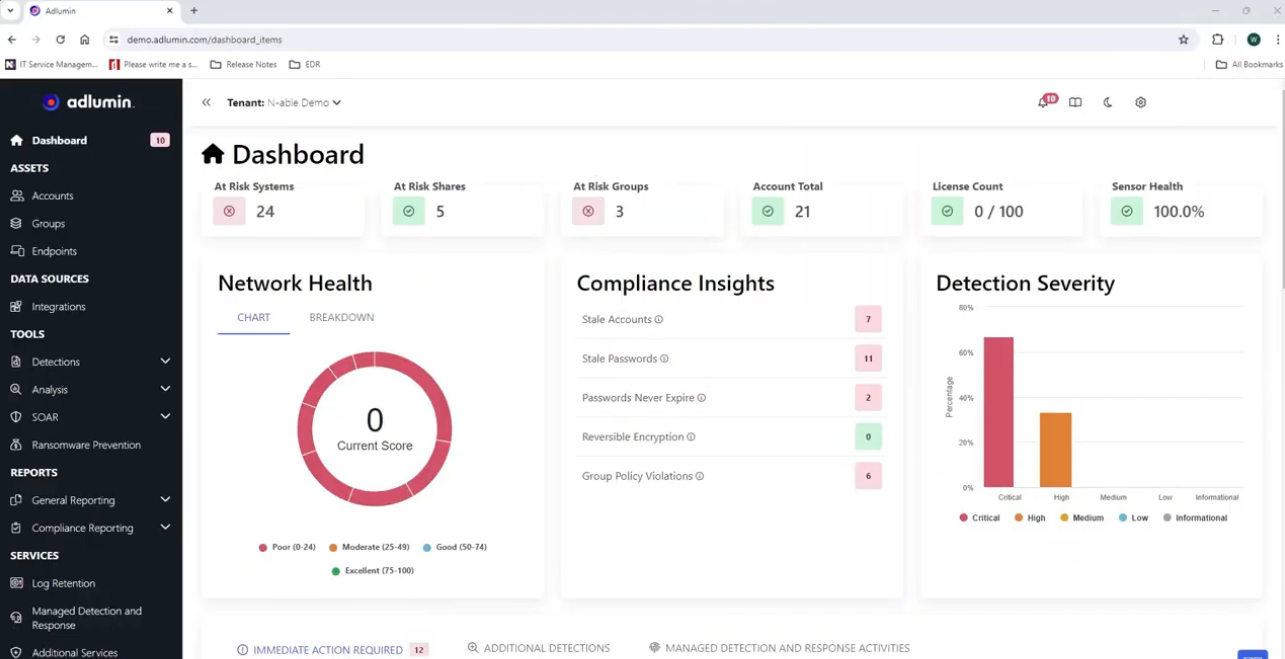
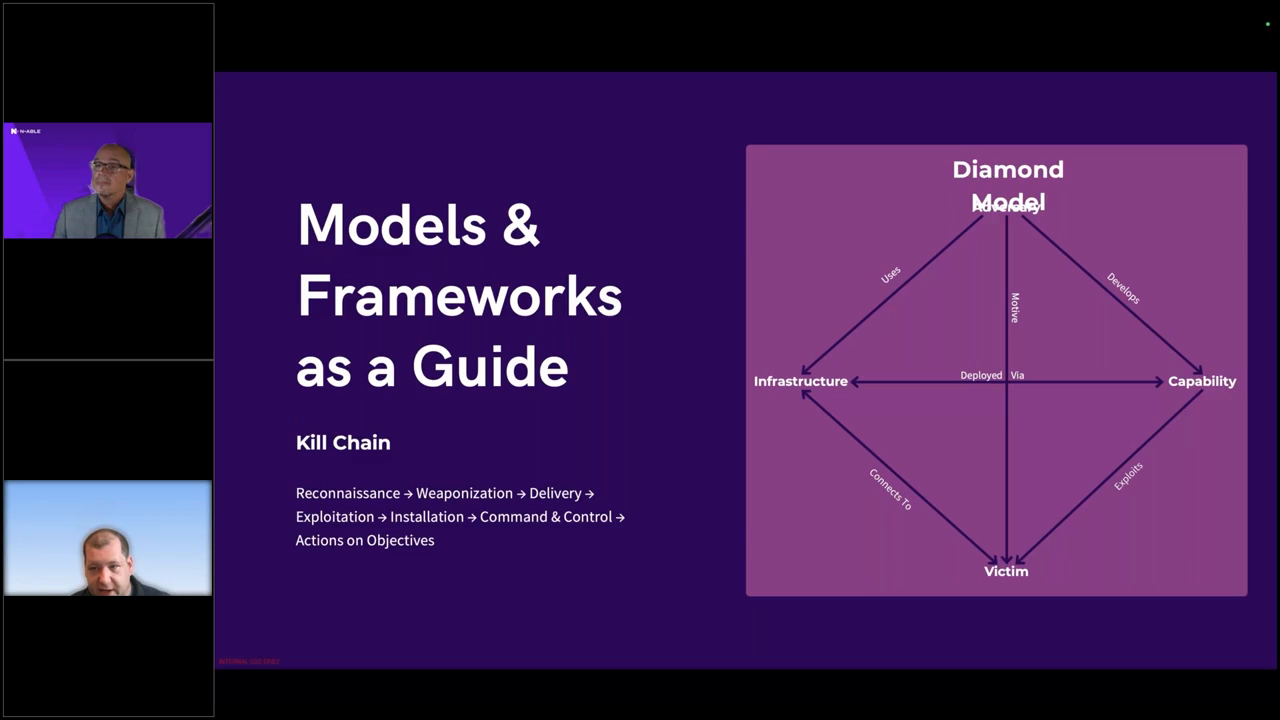
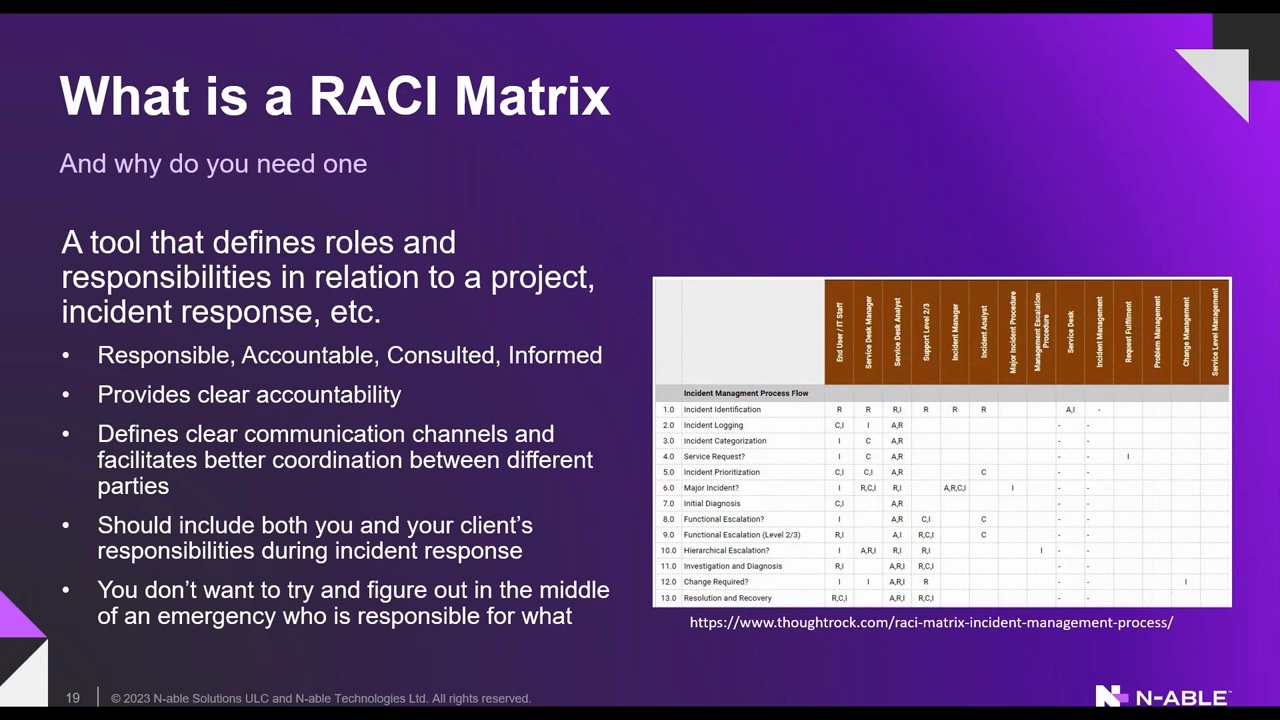
Healthcare Services Company Stops Brute Force Attack with Adlumin
Discover how a healthcare services company stopped a critical brute force attack before business hours with Adlumin MDR. This case study highlights 24×7 monitoring, rapid threat detection, and organization-wide visibility – learn how proactive security...