Five More Things You Might Not Know About N‑central

As I said the first time I wrote about this topic, “You don’t know what you don’t know.” In this blog, we’re going to look at five more things in N‑central that you might not know how to use—or you might not even know about them at all. If you haven’t read my first blog, check it out here.
1. Application compliance
As the number of end users working from home grows, so too will the number of unwanted applications on their remote devices. With the shift to cloud services, more and more new devices are no longer being deployed in restricted domain environments, which gives the end user the ability to have more freedom regarding what they install on their device. This isn’t always a good thing, and unwanted or undesirable applications can have a negative impact on a device’s performance.
Did you know that with N‑central you can leverage Application Compliance to be alerted when certain applications are detected on your managed devices? You can manually move discovered applications into Allowed, Disallowed, or Ignored groups at the Service Organization level, Customer level, Site level, or device level. Alternatively, you can create rules at that SO, Customer, or Site level to automatically classify discovered applications. For example, you could create a rule to mark an application as disallowed when the application name contains “torrent.”
While some people might be aware of the Application Compliance Rules and Settings under Configuration > Monitoring on the left navigation menu, the key for all this to work is to have the Application Compliance service added to the devices you want to monitor. You can either add the Application Compliance service to your existing default service templates for “Window – Workstations/Laptops and Servers,” or you can create custom templates to apply the service via a rule that leverages a custom property to cherry-pick the devices on which you want to enable it.
2. Integrated Cove Data Protection monitoring also works on devices with standalone Cove Data Protection
If you are using standalone Cove Data Protection and want to monitor it in N‑central, did you know you can use the integrated monitoring checks to do so? The N‑able Backup Monitoring template will not be automatically applied, so you’ll need to create a custom filter to find devices that have Cove Data Protection installed, but not through N‑central.
Check out an example of the settings you can use to build a filter for standalone Cove Data Protection devices in the screenshot below.
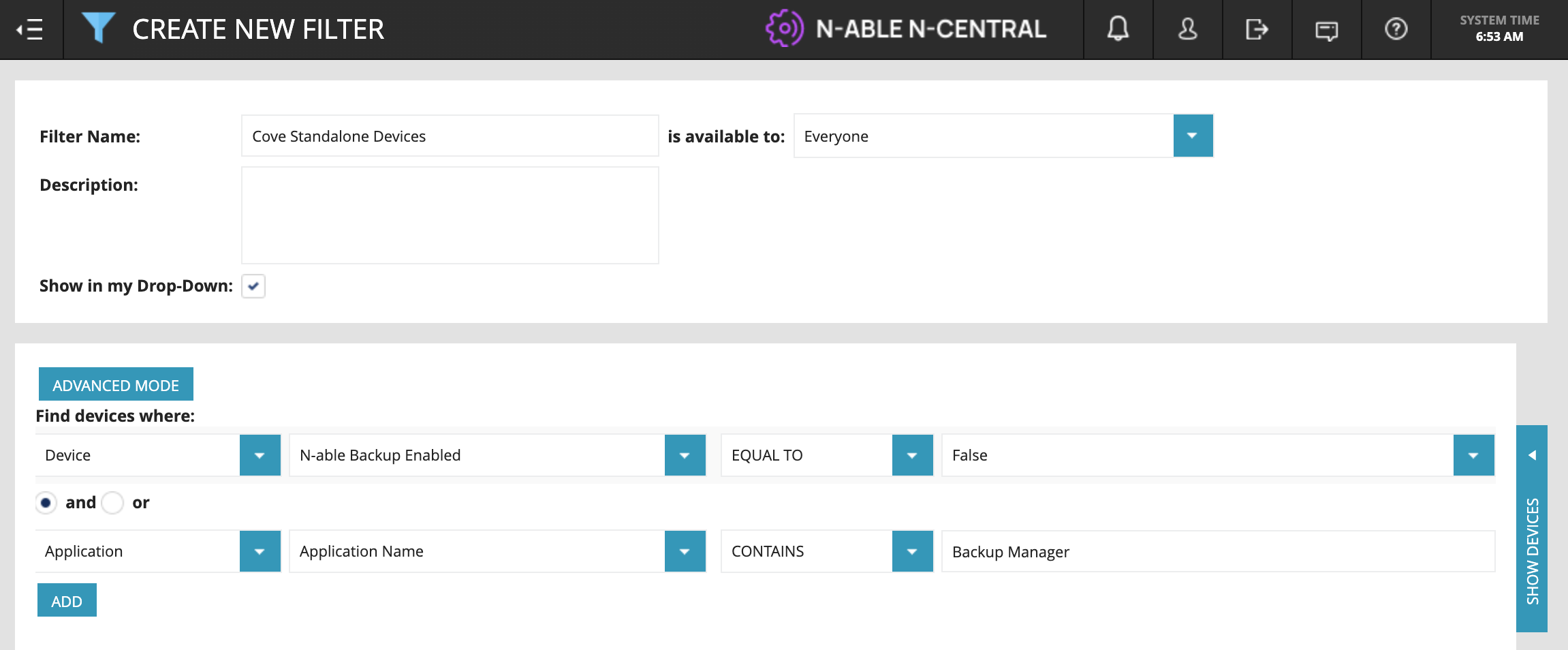
Applying the default templates will always flag a warning, as the service item “Installation Status” under the service “Backup Product Status” will state the product is not managed. To clear this, I recommend cloning the existing default templates, renaming the clones for standalone, and switching off the threshold for “Installation Status” under the service “Backup Product Status” in each of the three templates.

Then, using the filter you set up, create a rule to automatically deploy the monitoring to all standalone Cove devices.
3. Device notes can be kept indefinitely
Have you ever created a note on a device in N‑central and then wondered what happened to it when it’s gone months later? By default, device notes are retained only for a period of 100 days, but you can extend this retention up to 5,000 days, or better still set it to Unlimited Retention if you want to keep these notes indefinitely.
You can adjust this setting at the SO level for all devices or just for some customers and sites at those relevant levels as well. To do this, scroll down the left navigation menu to Administration > Defaults and click on Data Retention. You can then choose unlimited retention or specify a period of up to 5,000 days. Be sure to tick the Propagate box before you save to apply the changes to all the existing device notes as well.
4. Reporting on patches based on the KB number
When you learn of a new cyberattack, you need to move fast to ensure your devices under care are protected. Often this can be done by ensuring that the patch which addresses the vulnerability is installed, but how do you easily report that to your end customers? Well, did you know you can use the Patch Approvals and Installations report to do so?
At the customer level, go to Reports > Status and click on the Patch Approvals and Installations report. The “Search Patches by” field will default to Classification and Installation Result, but from the dropdown menu you can change this to KB Article Numbers, allowing you to find devices where specific patches are installed or not installed based on the KB number. This report will work even on devices that are currently not managed by N‑central’s patch management.
5. Compatibility mode for older OSs (self-hosted only)
In an ideal world, we would like all devices under management to be running the latest operating systems, but we know that’s likely never to be the case.
Since N‑central 12.3, Windows agents and probes have been updated to require TLS 1.2. This means that N‑central does not allow traffic over TLS 1.0. This causes any Windows agents or probes that are running older operating systems to lose the ability to communicate with your N‑central server.
Initially when we introduced this new security feature, the only way you could support older operating systems in your N‑central server was to switch the security profile to Legacy, which still supported TLS 1.0 and 1.1. But did you know there is now another more secure option called Compatibility mode?
The Compatibility security profile sits between the Legacy and Modern security profiles. It allows you to support older operating systems, such as Windows Server 2012 R2, but without allowing TLS 1.1 or 1.0. It disables weak SSH Ciphers, MACs, and KEX Algorithms, and it meets PCI requirements for TLS and ciphers.
We strongly recommend that you choose between either the Compatibility or Modern security profile. To check which settings you are currently using, log on to your N‑central server at the System level, go to Administration > Mail and Network Settings, then click on Network Security. Please note that if you intend to change these settings, you will need to reboot your N‑central server.
These are just some examples of areas of N‑central that partners and prospects may not be fully aware of. If you are reading this and have questions about anything here, why not join me on the N‑central office hours at www.n-able.com/events or reach out to me directly.
Paul Kelly is the Head Nerd at N‑able. You can follow him on Twitter at @HeadNerdPaul, LinkedIn and Reddit at u/Paul _Kelly
© N‑able Solutions ULC e N‑able Technologies Ltd. Todos os direitos reservados.
Este documento é fornecido apenas para fins informativos e não deve servir de base para aconselhamento jurídico. A N‑able não oferece nenhuma garantia, expressa ou implícita, nem assume qualquer responsabilidade legal ou responsabilidade pela precisão, integralidade ou utilidade de qualquer informação nele contido.
As marcas N-ABLE, N-CENTRAL e outras marcas registradas e logotipos N‑able são de propriedade exclusiva da N‑able Solutions ULC e da N‑able Technologies Ltd e podem ser marcas legais comuns, registradas ou de registro pendente com o Escritório de Marcas e Patentes dos EUA e com outros países. Todas as outras marcas comerciais mencionadas neste documento são usadas apenas para fins de identificação e são marcas comerciais (e poderão ser marcas registradas) de suas respectivas empresas.

