N‑able EDR in 2025: Autonomous Data-Rich Endpoint Defense for a Borderless World Landscape

In 2025 networks are everywhere – on-prem, in the cloud, and everywhere in between – so endpoint protection must be intelligent, autonomous, and resilient. It must be capable of defending users whether they’re on the corporate network, public Wi-Fi, or 35,000 feet in the air.
That’s not exactly what N‑able EDR delivers; it delivers way more.
AI-Powered Protection, Online or Off
N‑able EDR’s agent uses two types of smart detection to keep your business safe from cyber threats: Static AI and Behavioral AI.
Static AI works like a security scanner, checking files and programs before you open them to stop known threats right away. Behavioral AI watches how programs behave in real time, looking for any unusual or risky actions, even from new or unknown threats. Together, these technologies help prevent attacks before they start and catch sneaky threats as they happen, giving you peace of mind and protecting what matters to your business.
Whether a device is online or offline, the agent can autonomously mitigate or remediate threats, control USB access, and enforce policy, ensuring continuous protection without dependency on connectivity across the whole identified attack surface.
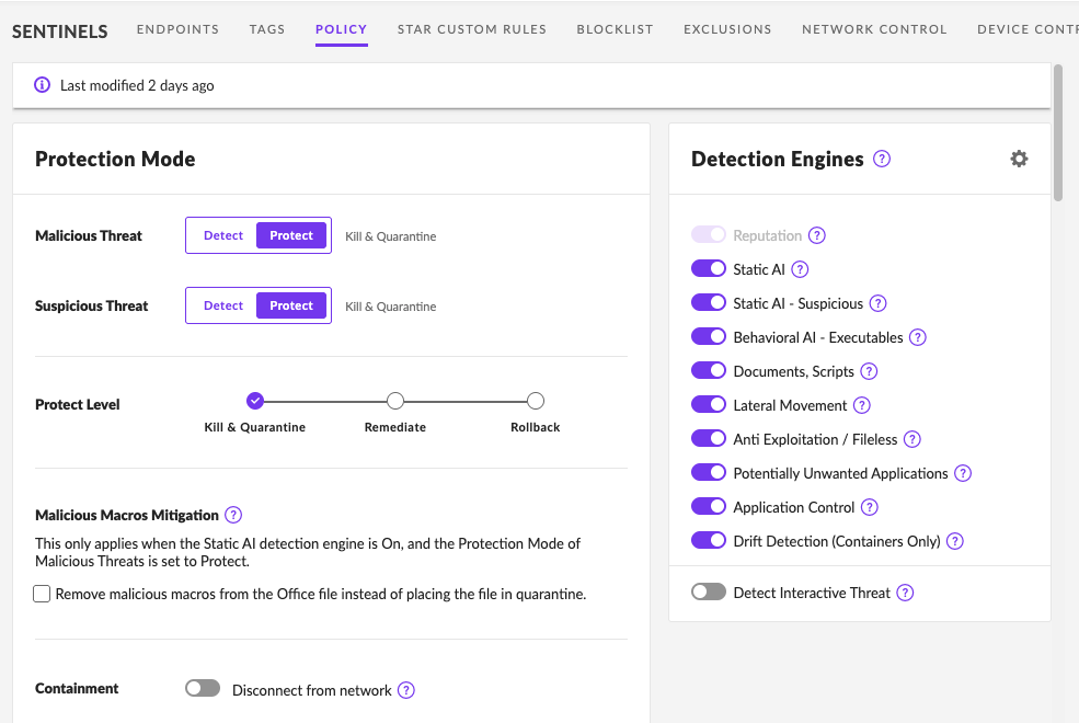
Resilience Through Patented One-click Remediation and Rollback
When prevention isn’t enough, N‑able EDR shows its value with its advanced endpoint protection. If ransomware or malware does slip through, security teams have access to a number of powerful features, including:
- One-click remediation of registry and file changes
- Rollback to a secured snapshot using VSS
- Global exclusion management to reduce false positives and minimize disruption
This means faster recovery, less downtime, and a reduced need to stop production to restore a system from backups unless absolutely necessary.
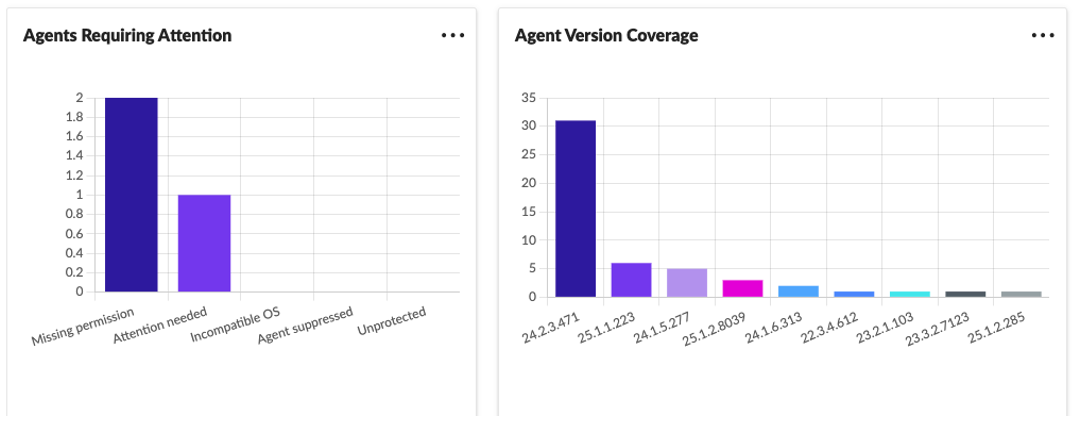
Unified Visibility and Control
The customizable dashboard offers a global view across customers and endpoints, surfacing unresolved threats, agent health, and incident status. The integration with N‑central and N‑sight ensures seamless deployment and monitoring – no manual token management or installer wrangling required.
Deep Threat Investigation and Hunting
Beyond real-time protection, N‑able EDR empowers deep post-execution analysis, giving security teams the tools to investigate, hunt, and respond with precision. The Threat Hunting functionality in N‑able EDR makes it easier to investigate potential threats by allowing analysts to group and examine threats based on their file hash. This streamlines the triage process, helping teams quickly identify and assess risks.
Analysts can drill into:
- Originating processes
- Industry leading analysis of threat indicators. For the fourth consecutive year SentinelOne, which powers N‑able EDR, has ranked among the top performers in the MITRE ATT&CK® Evaluations, achieving 100% detection, zero delays, and 88% fewer alerts than the median vendor.
- Virus Total lookups
- Full process trees and behavioral timelines
The Deep Visibility capability provides a “CCTV-like” retrospective view of all device activity — such as DNS queries, logins, and process launches — helping to enable forensic analysis and proactive threat hunting across the network perimeter. Whether you’re a seasoned analyst or just starting out, this level of insight can help your teams investigate faster and respond smarter.
Policy-Driven Endpoint Protection and Automation
From USB control to firewall rules, N‑able Advanced Endpoint Protection empowers granular policy configuration. It allows you to:
- Block or allow devices by type, vendor, or serial number
- Prevent unauthorized agent downgrades
- Automate decommissioning of inactive devices
- Isolate infected endpoints while maintaining remote access via Take Control
This ensures security without sacrificing manageability or user productivity.
Network Discovery and Application View
EDR agents can scan the network to identify unprotected endpoints — such as, printers, IoT, or rogue laptops — and either isolate them or deploy agents directly. The Application View capability highlights vulnerable software, helping teams prioritize patching and reduce attack surface.
Integrated Threat Response and Managed Services
N‑able EDR integrates seamlessly with N‑central and N‑sight, enabling:
- One-click deployment at scale
- Network health and threat telemetry ingestion
- Automated ticketing and self-healing workflows
For organizations seeking additional support, we offer a fully managed SOC experience. This provides broader telemetry coverage as well as alerting and containment capabilities.
It’s Cybersecurity, So Outcomes Do Matter
Ultimately, N‑able EDR’s advanced endpoint protection is designed to drive better outcomes, and that’s the advantage it aims to deliver:
- Accelerated detection and response capabilities
- Potential for reduced operational overhead
- Enhanced cybersecurity functionality
- A robust security posture from the start
Whether you’re an MSP scaling your security services or an enterprise IT team safeguarding a distributed workforce, N‑able EDR provides the deep visibility, automation, and rich data telemetry you need to stay ahead of threats — while also helping to support compliance and cyber insurance requirements.
And now, with a new wave of innovations purpose-built for modern security operations, that advantage only grows.
What’s New in 2025: More Data, More Insight, More Autonomous Oversight
In 2025, N‑able EDR isn’t just about stopping threats, it’s about giving you the tools to outpace them. That’s why we’re excited to introduce three powerful enhancements that can help take your security operations to the next level:
- Flexible Data Retention: From 14 days to 365, you now have full control over how long you keep your data. Whether you’re meeting compliance mandates, conducting deep forensic investigations, or proactively threat hunting, you’ll have the historical visibility you need.
- Cloud Funnel: Stream enriched XDR telemetry in real time to your own Azure storage. No more manual exports. No more silos. Just seamless integration with your SIEM, SOAR, or analytics tools, so you can correlate across your entire ecosystem and retain data on your terms.
- AI Security Analyst (powered by SentinelOne’s PurpleAI™ technology): Meet your AI-powered security analyst. Built on the Open Cybersecurity Schema Framework (OCSF), it helps you detect earlier, investigate faster, and respond smarter. With natural language threat hunting, contextual insights, and self-documenting investigations, it’s like adding a senior analyst to your team, without adding headcount, while also giving junior analysts the confidence, context, and guidance to operate at a whole new level.
These aren’t just features—they’re force multipliers. They help you deliver stronger outcomes, faster response, and smarter security at scale.
Real People. Real Outcomes. No dream scenarios.
See our newest video on how ITC used N‑able EDR to deliver peace of mind to growing businesses and transform its security practice into a growth engine.
Cybersecurity without compromise starts here.
Ovidiu Cobzaru is Senior Product Marketing Manager at N‑able
© N‑able Solutions ULC e N‑able Technologies Ltd. Todos os direitos reservados.
Este documento é fornecido apenas para fins informativos e não deve servir de base para aconselhamento jurídico. A N‑able não oferece nenhuma garantia, expressa ou implícita, nem assume qualquer responsabilidade legal ou responsabilidade pela precisão, integralidade ou utilidade de qualquer informação nele contido.
As marcas N-ABLE, N-CENTRAL e outras marcas registradas e logotipos N‑able são de propriedade exclusiva da N‑able Solutions ULC e da N‑able Technologies Ltd e podem ser marcas legais comuns, registradas ou de registro pendente com o Escritório de Marcas e Patentes dos EUA e com outros países. Todas as outras marcas comerciais mencionadas neste documento são usadas apenas para fins de identificação e são marcas comerciais (e poderão ser marcas registradas) de suas respectivas empresas.

