Solutions for IT Departments Streamline your IT operations

N‑able’s products build ease and efficiency into all functions of IT, from endpoint management to backup and security, all from a single web interface.
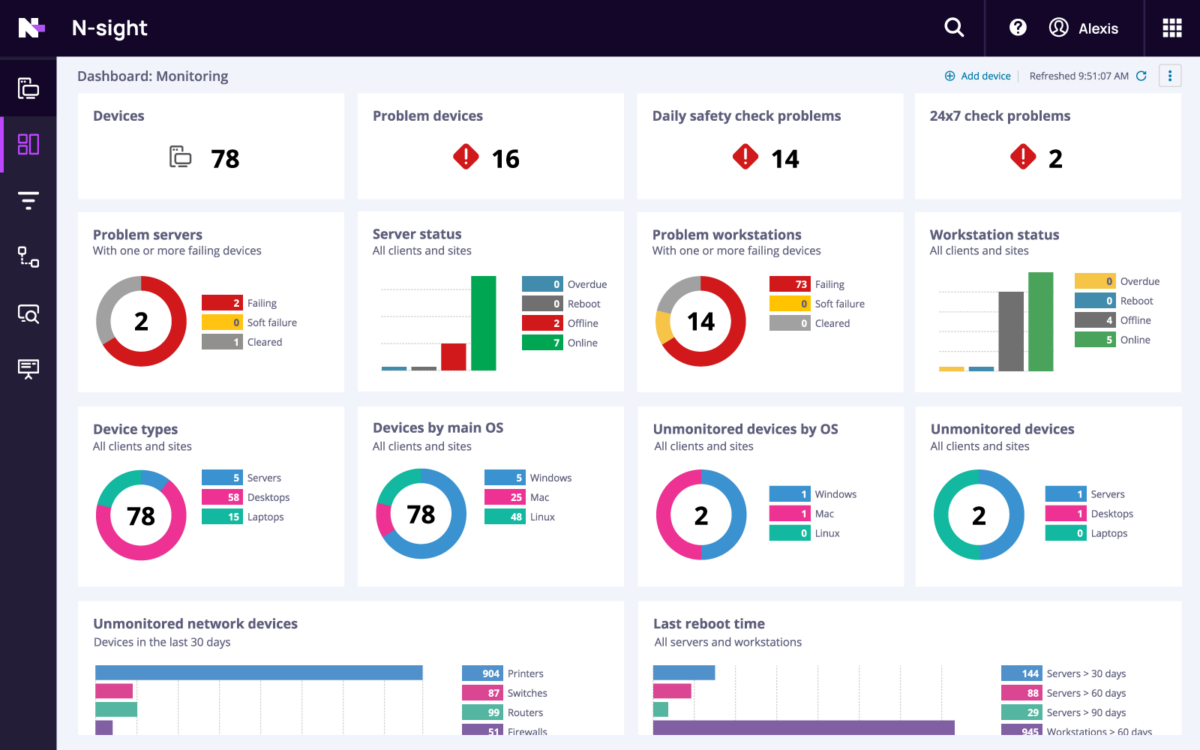
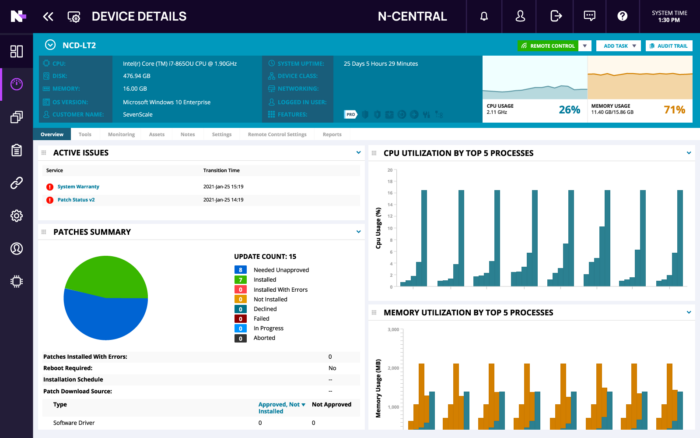
Complete, cloud-based control over every endpoint from a single dashboard
Proactively monitor all of your networks and devices with unified endpoint management through N‑able RMM (Remote Monitoring and Management) platforms. Keep devices compliant and secure with flexible patch management.
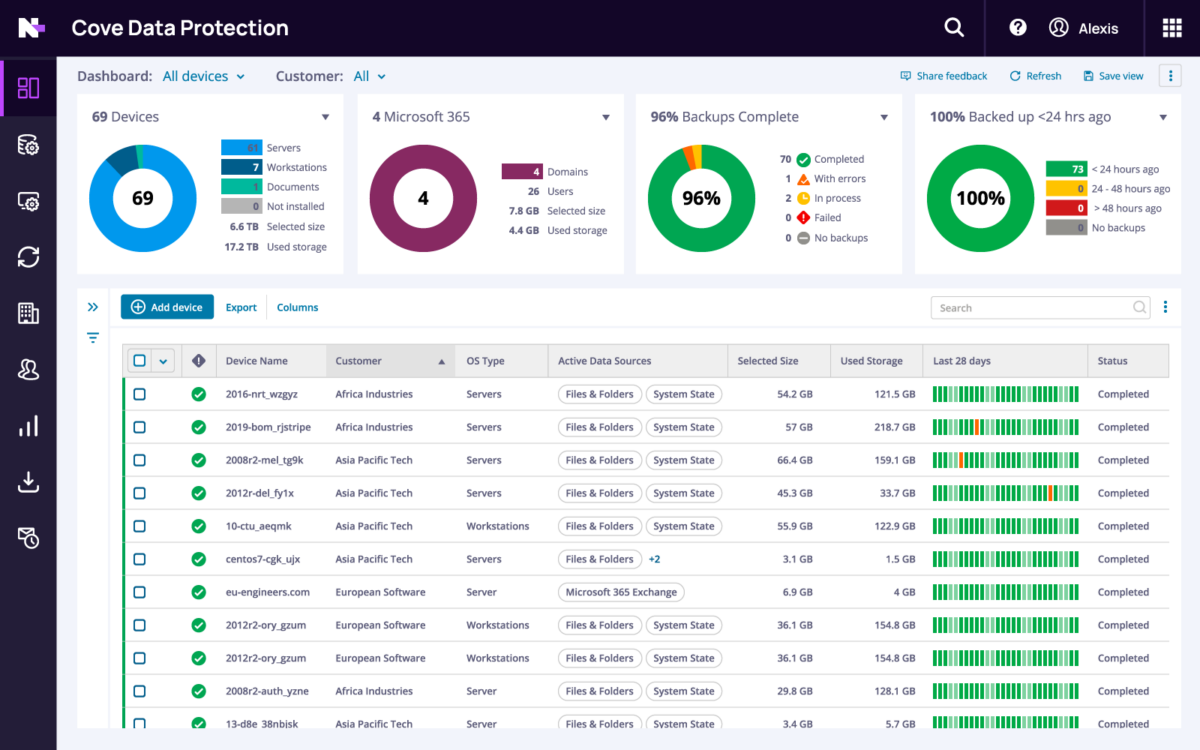
Comprehensive backup and recovery for servers, workstations, and Microsoft 365
With the growth of ransomware, cloud-first and SaaS-based data protection is becoming a critical element in data recovery. A unified dashboard simplifies management and allows IT to focus on more strategic work.
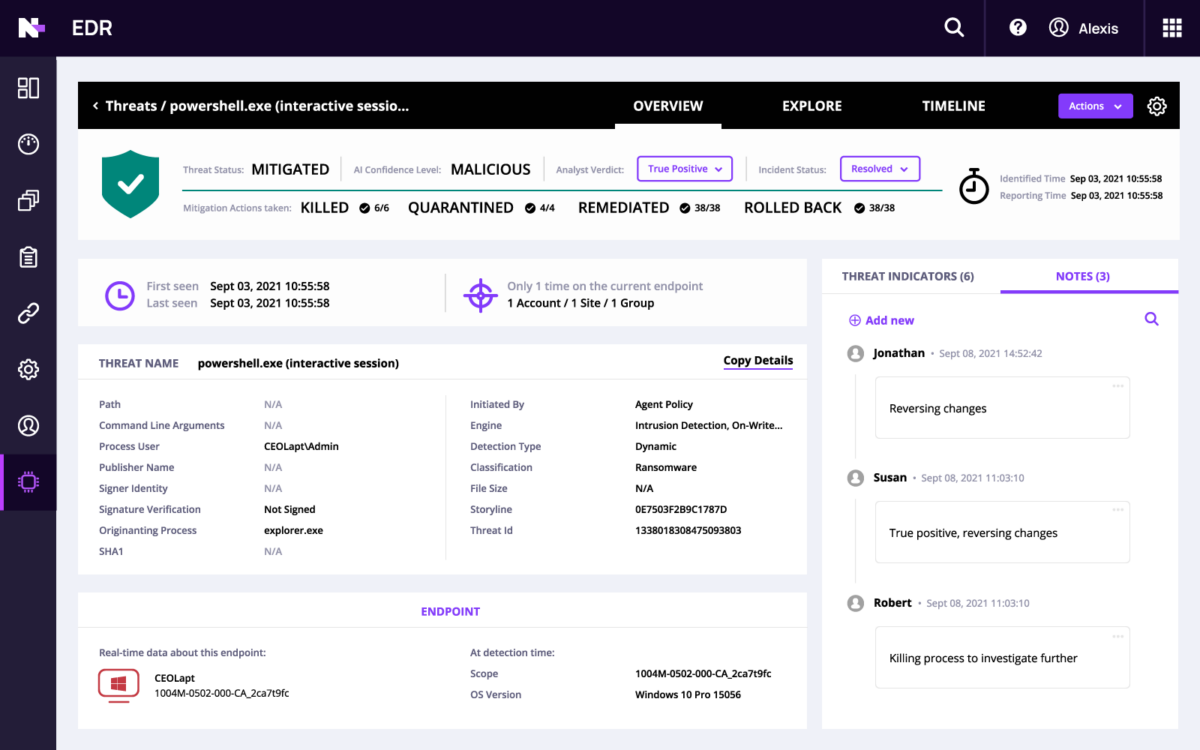
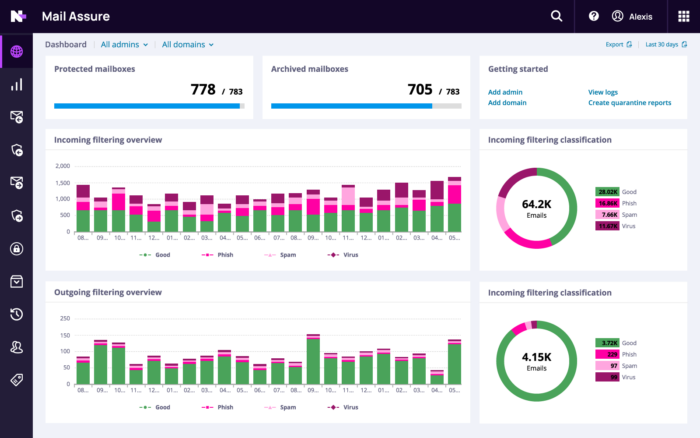
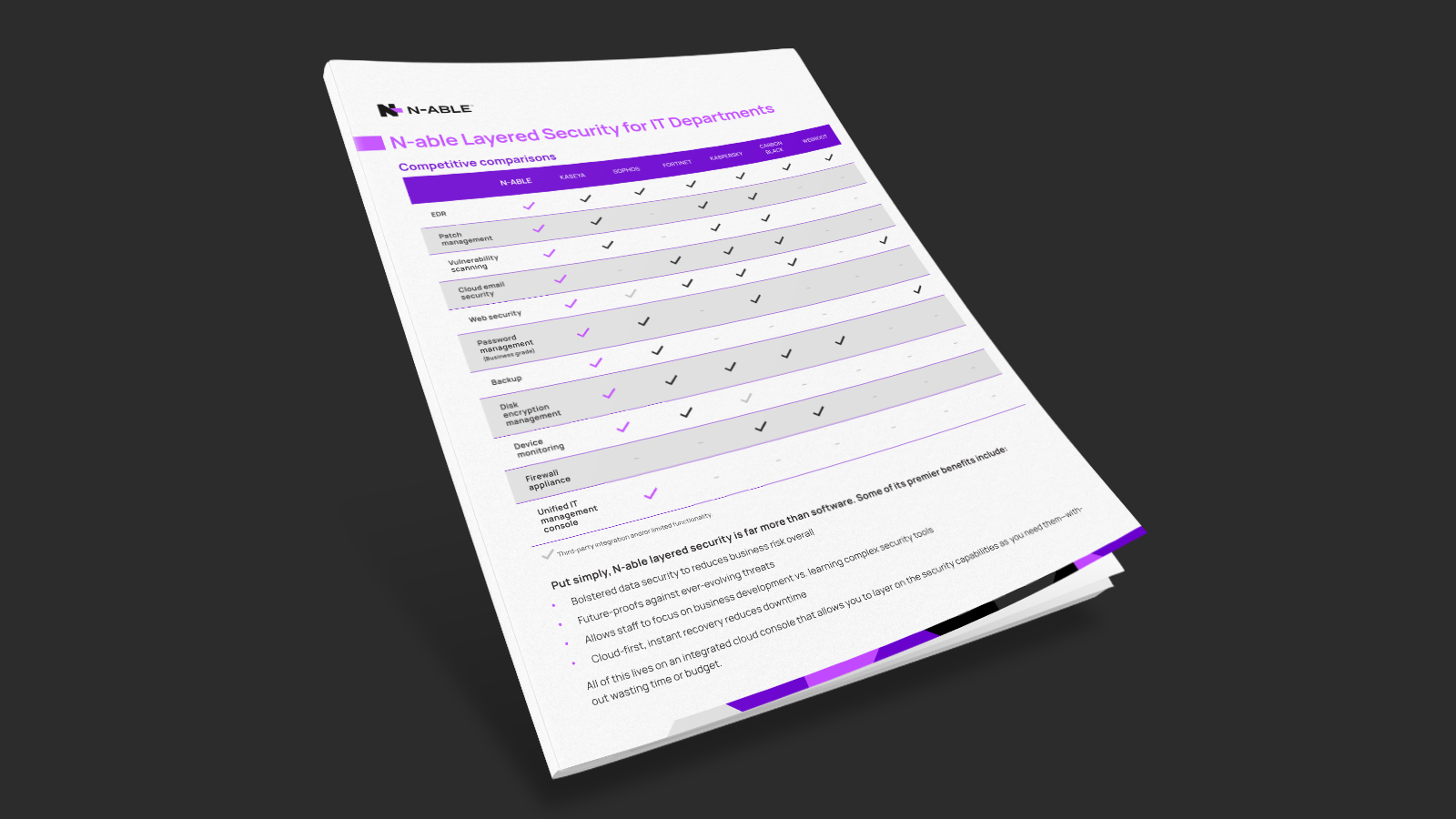
Advanced threat protection that goes beyond AV
Antivirus and firewalls are often not enough protection. Modern criminals frequently use multiple methods of attack, which is why N‑able offers a range of security layers to help you stay protected.
Proud to be trusted by






Why internal IT teams need N‑able
Build efficiency through standardization
Build efficiency through standardization
Increasing dependance on third-party solutions expands the risk of exposure. Standardizing RMM across an entire business creates a solid bedrock for a successful IT department, helping reduce overall risk and attack surface.
Reduce labor costs with automation
Reduce labor costs with automation
Automation is key to boosting productivity and efficiency, while reducing unexpected results and human error. N‑able’s RMM platforms feature an integrated automation manager to easily create policies designed to deliver faster, more consistent service.
Be disaster ready
Be disaster ready
After a cyberattack, recovery back to the original production environment can risk malware re-infection. Cove’s cloud-first architecture stores your backups offsite by default—a modern best practice—helping business to continue as usual.
Help meet insurance requirements
Help meet insurance requirements
With the rise in ransomware attacks and data breaches, some tools, such as Endpoint Detection and Response and modern off-site-first data protection, are becoming “must-haves” for cyber insurance coverage.
Efficiently manage, secure,
and automate.

Patch across Windows, Mac, Linux, and more
N‑able’s flexible patch management solutions deploy OS and third party updates to help keep devices compliant and secure, across a variety of platforms.
Lower the risk for your business before you are attacked
Device layer protection focuses on detecting and preventing attacks, helping your limited security budget go further.
- Managed Antivirus for easily deployed and managed baseline protection
- Endpoint Detection and Response to prevent, detect, and respond to ever-changing threats
- Cloud-based email security to provide continuity and long-term email archiving
- DNS Filtering to protect users on and off networks
- Standby Image Backup to get ahead of disaster recovery and make it more predictable
Secure your remote connections end-to-end
To keep systems up and running you need tools that allow you to get to and solve issues faster. Our remote access solution puts any of your organization’s devices at your fingertips.
I can confidently say that Adlumin MDR proved its value within the first six hours of deployment. We received alerts that our Police Department was being hit thousands of times by somebody trying to get in. Adlumin MDR notified us immediately and we isolated that workstation before the intruders were able to get into our network and do any damage.
James E Pacanowski II CGCIO/Network Administrator, City of Ventnor
We acquired the Cove backup solution in conjunction with N‑central. We encountered a critical incident where all our virtual Domain Controllers went offline, rendering workstations inaccessible. Thanks to Cove Data Protection, we efficiently restored the server without a hitch, and within an hour, we were back in operation! We are grateful for Cove’s reliable and user-friendly solution.
Robert McQueen IT Director, Township of Franklin
With Cove, we’ve enhanced the efficiency of our internal operations and elevated the level of service and reliability we offer to dental practices across the country. It’s truly been a game changer for our organization and the dental community we serve.
John Paul B. Murphy Head of Business Applications & IT, Dandy
The N‑able difference
An all-in-one solution
Onboard on the double
Cost predictability
Get scalable solutions with low cost of ownership to help manage your IT software costs.
Customer Experiences
in their own words
“N‑central has really enabled SRP to gain valuable insights into our infrastructure, leading into informed decision making and optimizing of our resources. We have experienced a notable decrease in downtime ensuring continuous operations and productivity thanks to pro-active monitoring and issues detection.”
“One of the highlights for Fusion Health is the self-healing aspect of using the N‑central platform. We were able to use client server technology, do break fix methods and actually restore these things automatically as opposed to getting manual intervention in place. This has prevented probably hours of manual labor on a week to week basis.”
"We chose N‑able N‑central mostly for reliability and scalability as we have a lot of devices that we send out, so we wanted to make sure that we can grow with it. It has been really reliable for us. It has been really easy to implement, we have tons of devices and a lot of traffic load for our unique use case. It has been really helpful for us."
"One of the highlights for First Watch restaurants about N‑able’s N‑central solution has been the ease of rolling it out. We were managed by a different MSP and bringing in N‑central, I was able to roll-out the product in basically less than a day and actually use it and got rid of the other tool that the company was using."
Resources
Connect with our experts
N‑able is passionate about helping all IT professionals keep their organizations safe, secure, and successful. Let our network of experts help you:
- Learn more about our solutions, products, and pricing
- Get in contact with a partner in your local area
- Sign up and start enjoying the benefits of N‑able
Talk with a specialist about IT solutions
The DELL TECHNOLOGIES logo is a trademark of Dell Inc.