Threat Hunting Hunt smarter. Protect endpoints faster.

Give your security team the tools to detect, respond, and win against threats.
*Terms and conditions apply.
Threat hunting platform with AI-driven automation and rapid remediation
**IDC Business Value of SentinelOne’s PurpleAI, July 2025
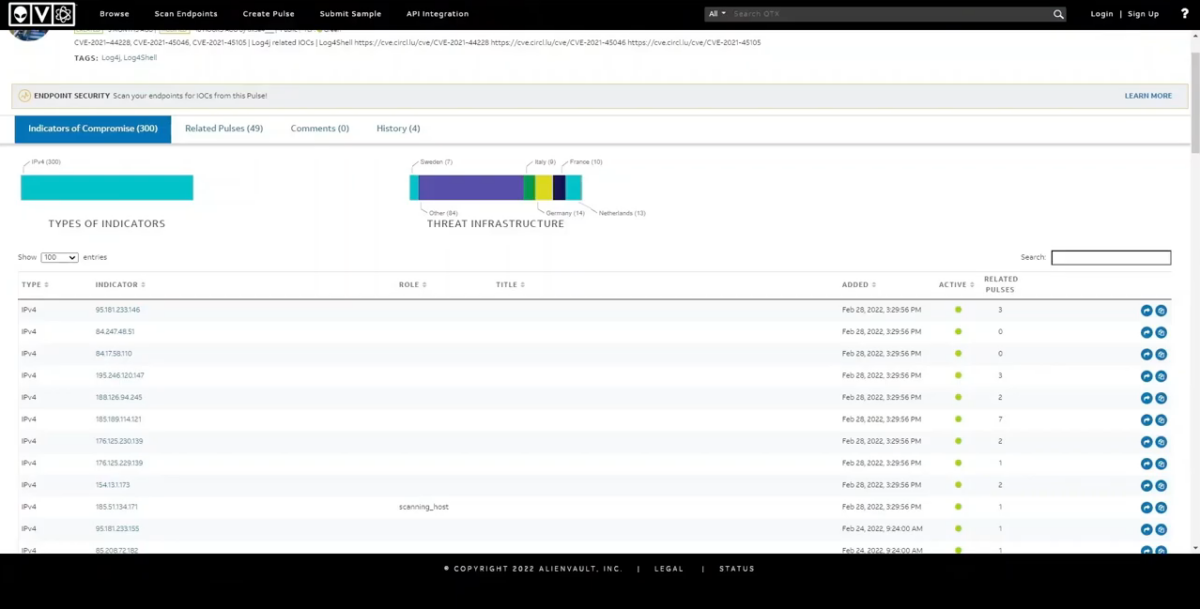
Gain deep visibility across endpoints
Detect stealthy attacks using endpoint detection and response tools and AI-driven correlation. Maintain long-term data retention to support audits and post-incident reviews
Out-of-the-box automation makes the solution easy to deploy and operate, while the threat intelligence, advanced artificial intelligence, and machine learning secures our customer’s endpoints.
Out-of-the-box automation makes the solution easy to deploy and operate, while the threat intelligence, advanced artificial intelligence, and machine learning secures our customer’s endpoints.
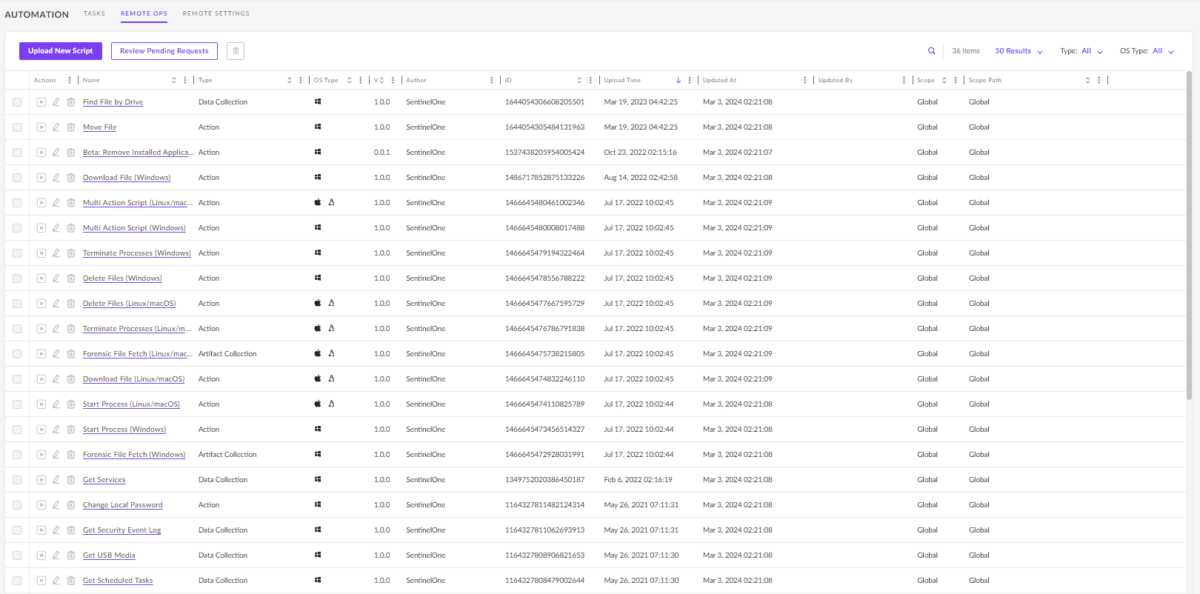
Rapid remediation and continuous protection
Rapid remediation and continuous protection
When an incident occurs, threat hunting tools reveal the full story: root cause, propagation, and impact
Reduce manual effort and optimize resource use
Reduce manual effort and optimize resource use
Threat hunting platform that boosts SOC productivity. Scale security impact with AI-driven efficiency and long-term data retention
Enhance analyst output and reduce manual overhead
Enhance analyst output and reduce manual overhead
Threat hunting platform with activity visualizations and AI-driven remediation. Resolve threats quickly and retain data for audit and insurance needs
Proactive threat hunting that reinforces your security resilience
Proactive threat hunting that reinforces your security resilience
Proactively mitigate potential threats and avoid downtime risks. Ensure business-as-usual to help keep cybersecurity insurance costs down

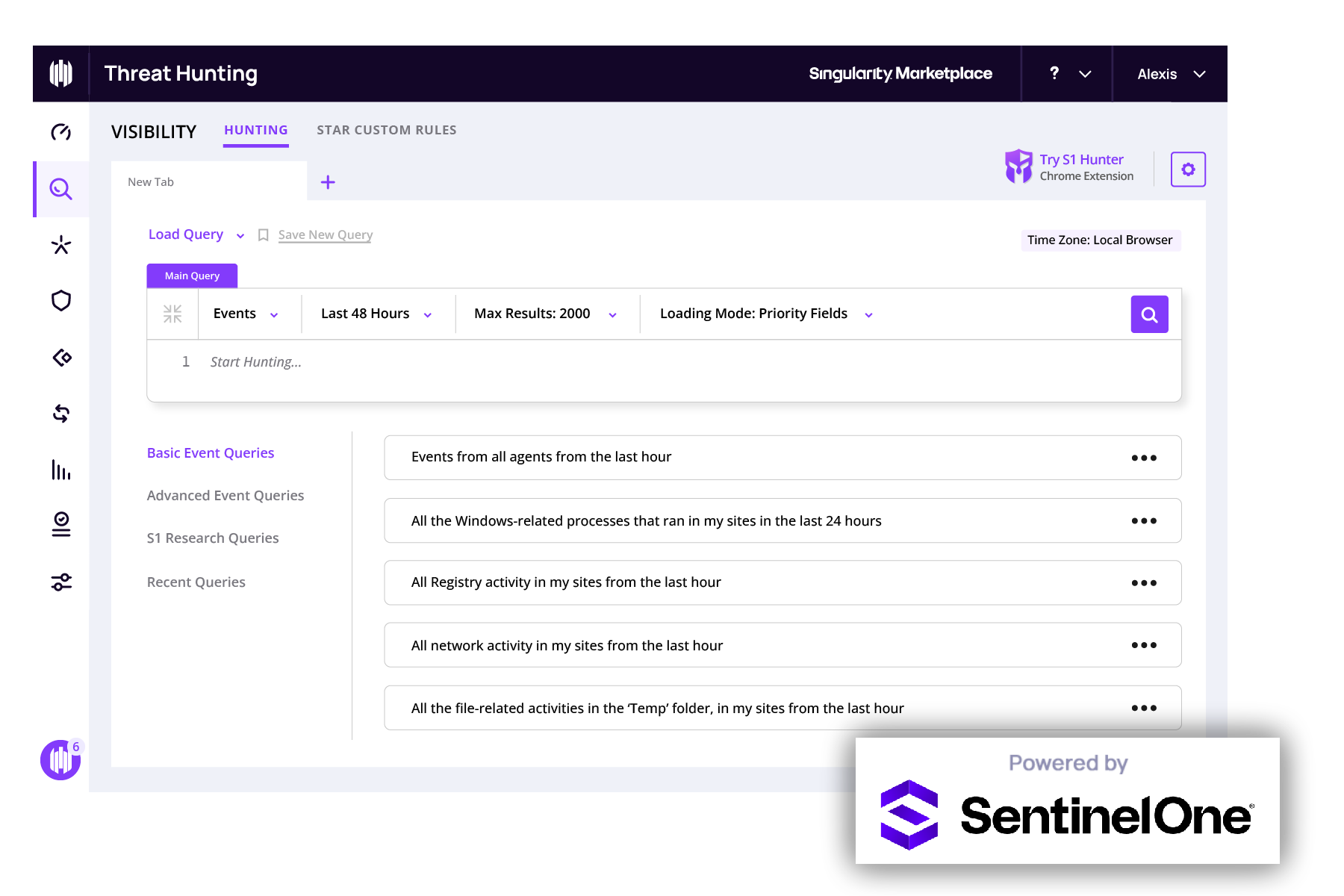
Reveal full threat context and root cause
Understand what happened and why with AI-assisted threat hunting that reveals the root cause, propagation, and impact. Retain data across quarters for insurance, compliance, and strategic defense.

Automate SOC processes
Automate SOC workflows with AI-powered threat hunting services—correlate MITRE detections into unified threat chains and resolve incidents with one-click remediation.
Advance your SOC with AI-powered threat hunting services
N‑able Managed EDR connects your organization to SentinelOne Vigilance, a 24×7 team of cybersecurity experts who proactively hunt and neutralize threats. With advanced software and platform-level visibility, they reduce alert fatigue and let your SOC focus on cyber resilience
Our EDR partner, SentinelOne®, continues to be a Top Performer in the MITRE 2024 Evaluations
Demonstrating an outstanding signal-to-noise ratio. Security teams that can avoid alert fatigue stay ahead of adversaries, rapidly responding to legitimate threats while safeguarding their operations and customers.
For the fifth consecutive year, the Singularity Platform delivered a flawless detection performance, achieving 100% detection at major step level.
Zero detection delays across all simulated attack scenarios.
Scored perfect on detections for attack techniques simulated across Windows, MacOS and Linux systems.
Resources
FAQ
1. What is threat hunting?
1. What is threat hunting?
Threat hunting, also known as cyber threat hunting, is a proactive cybersecurity practice that helps uncover hidden threats and vulnerabilities across an organization’s attack surface. Using expert-driven hypotheses and advanced threat hunting tools, it enables faster incident response and reduces overall risk.
2. How does cyber threat hunting work?
2. How does cyber threat hunting work?
Threat hunting assumes attackers may already be inside your environment. It begins with a hypothesis, followed by investigation, and—if confirmed—leads to threat response and remediation. Effective threat hunting requires deep knowledge of normal system behavior to spot anomalies like attacker TTPs, vulnerable entry points, and indicators of compromise.
3. What are threat hunting tools?
3. What are threat hunting tools?
Effective threat hunting requires visibility across endpoints, threat intelligence, and skilled security professionals. While expertise is essential, visibility and intelligence can be gained through automated threat hunting tools like EDR, XDR, SIEM, IDS/IPS, and AI-powered analytics. These tools help centralize endpoint telemetry, correlate events, and monitor threats in real time. Threat hunters also use threat intelligence feeds to validate hypotheses and search for indicators of compromise across the attack surface.
4. How can the MITRE ATT&CK framework be leveraged in threat hunting?
4. How can the MITRE ATT&CK framework be leveraged in threat hunting?
MITRE ATT&CK® is a widely used framework that categorizes adversary tactics and techniques based on real-world behavior. It provides threat hunters with a common language and actionable insights into attacker methods, motivations, and response strategies. N‑able EDR with Threat Hunting, powered by SentinelOne®, maps threats to the MITRE ATT&CK matrix—enabling analysts to identify malicious behavior across endpoints using threat hunting tools and indicators of compromise.
5. Where does proactive threat hunting fit in with your security strategy?
5. Where does proactive threat hunting fit in with your security strategy?
Proactive threat hunting helps accelerate incident response, reduce SOC workload, and improve visibility into emerging threats. Whether you’re running an internal SOC or supporting clients, threat hunting strengthens your security stack. Solutions like N‑able EDR with Threat Hunting offer the threat hunting tools and platform capabilities needed to build or enhance a program.
Want to learn more?
The advanced Threat Hunting feature of N‑able EDR helps you actively hunt for threats and stop them before it’s too late. Connect with our security experts to learn more.