
Attack Surface Management Discover hidden network assets

Deep visibility across BYOD, IoT, and unknown endpoints.
How Attack Surface Management works

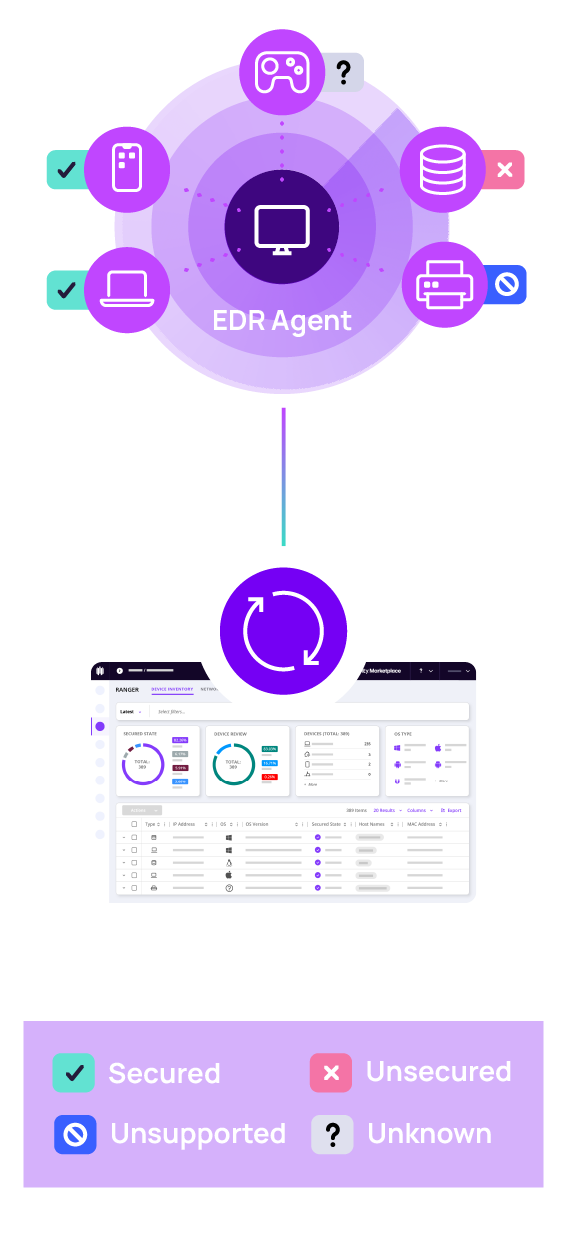
The benefits of Attack Surface Management with N‑able EDR
Get up and running in no time
Extend N‑able EDR to full network visibility, no added software, hardware, or deployment effort.
Automate heavy lifting
Consolidate network tools into one console, minimize friction with attack surface.
Know your network – no blind spots
With Attack Surface Management, we accurately scan for hidden or stealth endpoints so they do not go unnoticed. Advanced network scanning reveals every device—BYOD, IoT, and rogue assets, monitoring their communication patterns for full visibility.
Flexible network scanning
Control what’s scanned, when, and how, by subnet or prompt. Enable the PurpleAI Security Analyst responding to natural language commands to do network scans.
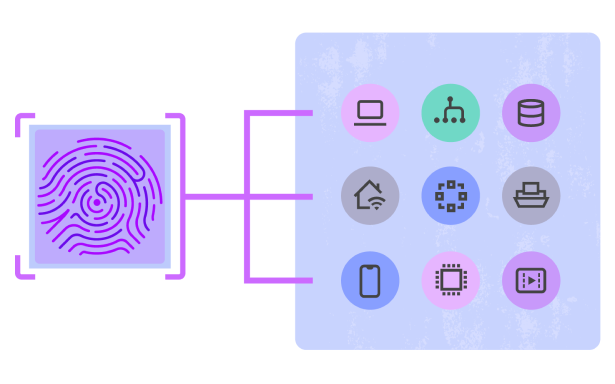
Unsecured but not undiscovered
Create and update asset inventories with every scan, then close gaps fast using prompt-driven peer-to-peer agent deployment via the EDR console.
Fingerprint security at your fingertips
When an unknown device appears, it’s fingerprinted, categorized, and isolated instantly.
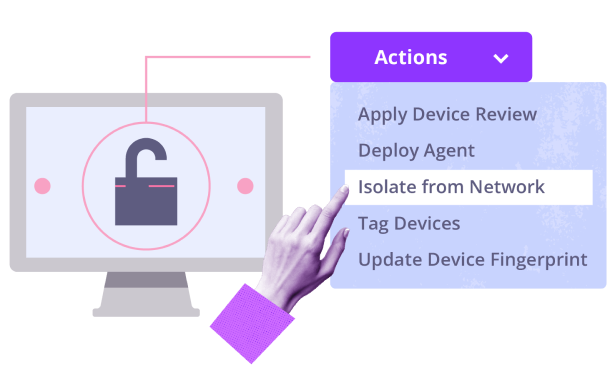
Reduce and control the attack surface
Incident readiness starts with visibility—know every device, its risk level, and how to respond.
Investigate and respond fast
Hunt threats with enriched device intelligence then pivot to lateral movement investigations using PurpleAI Security Analyst prompts.
Resources
N‑able EDR: Attack Surface Management
Speak to an expert
You’ve seen the advantages of Attack Surface Management. Now let’s talk about how we can use them to help your business reach peak device visibility.




