Endpoint Detection and Response AI-powered endpoint security for proactive threat defense

Detect threats early and maintain smooth operations with AI-enhanced security. Built for rapid response and resilience.
Automation for operational excellence, preserving business continuity
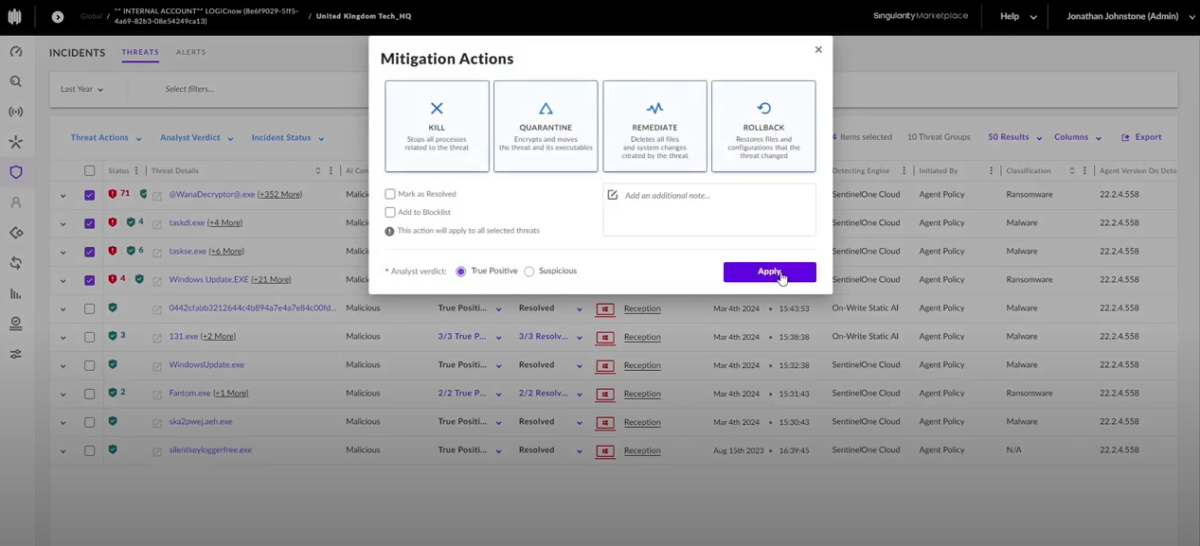
Instantly contain threats, auto-remediate malicious changes, and roll back devices in seconds.
There are more attacks and now customers are more aware of the need for better services, and even small businesses are pushing for better tools and services.
In the mid-market and enterprise arenas, customers are asking for more co-managed models, bringing in specialists for the most skilled elements of cybersecurity solutions.
There are more attacks and now customers are more aware of the need for better services, and even small businesses are pushing for better tools and services.
In the mid-market and enterprise arenas, customers are asking for more co-managed models, bringing in specialists for the most skilled elements of cybersecurity solutions.
Unified endpoint protection made easy
Unified endpoint protection made easy
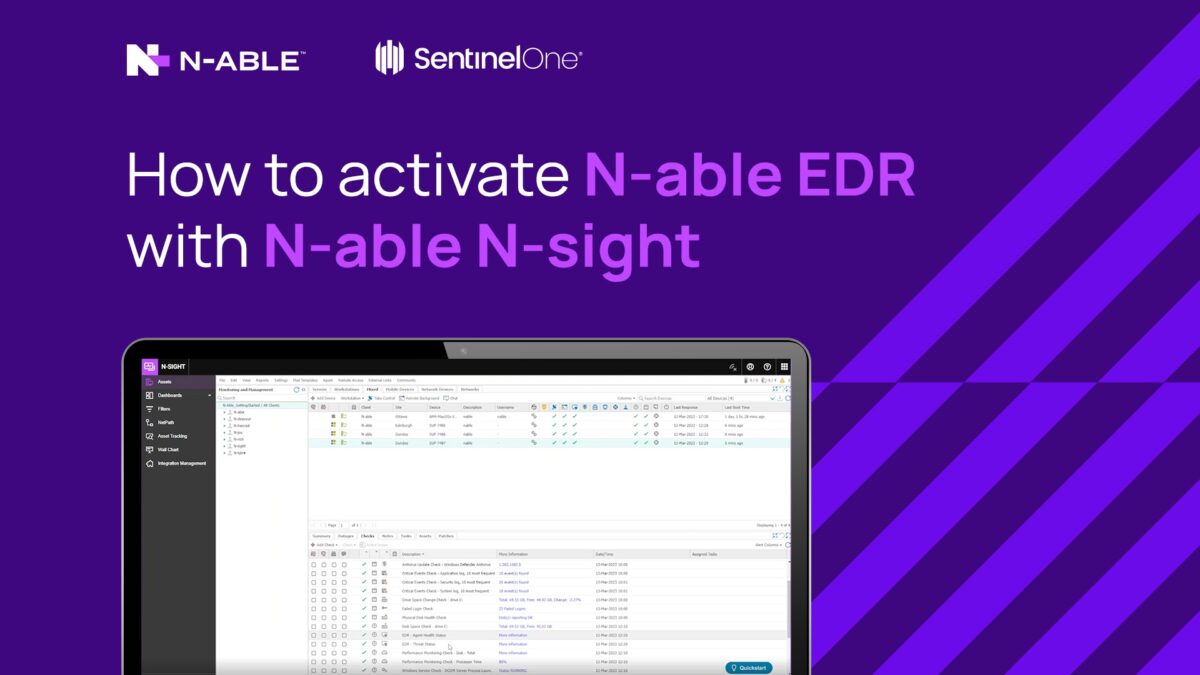
Access EDR from your N‑central® or N‑sight™ dashboard, apply policies quickly, and remediate threats instantly without scans or signature updates.
Easily demonstrate value
Easily demonstrate value
Incident response begins the moment a threat is detected: automated rollback and forensic clarity built in
Support cyber insurance readiness
Support cyber insurance readiness
Strengthen your security posture with autonomous protection and forensic-level visibility—demonstrating business resilience and reducing risk exposure.
Scale your business with expert-backed EDR solutions
Scale your business with expert-backed EDR solutions
Tap into expert-led endpoint security resources—from Head Nerds and N‑able U to MarketBuilder campaigns—all designed to accelerate your cybersecurity strategy and drive business growth.
Easily deploy EDR
Deliver lasting endpoint protection with automated policy enforcement and rapid deployment, ensuring continuous operations and full control across environments.
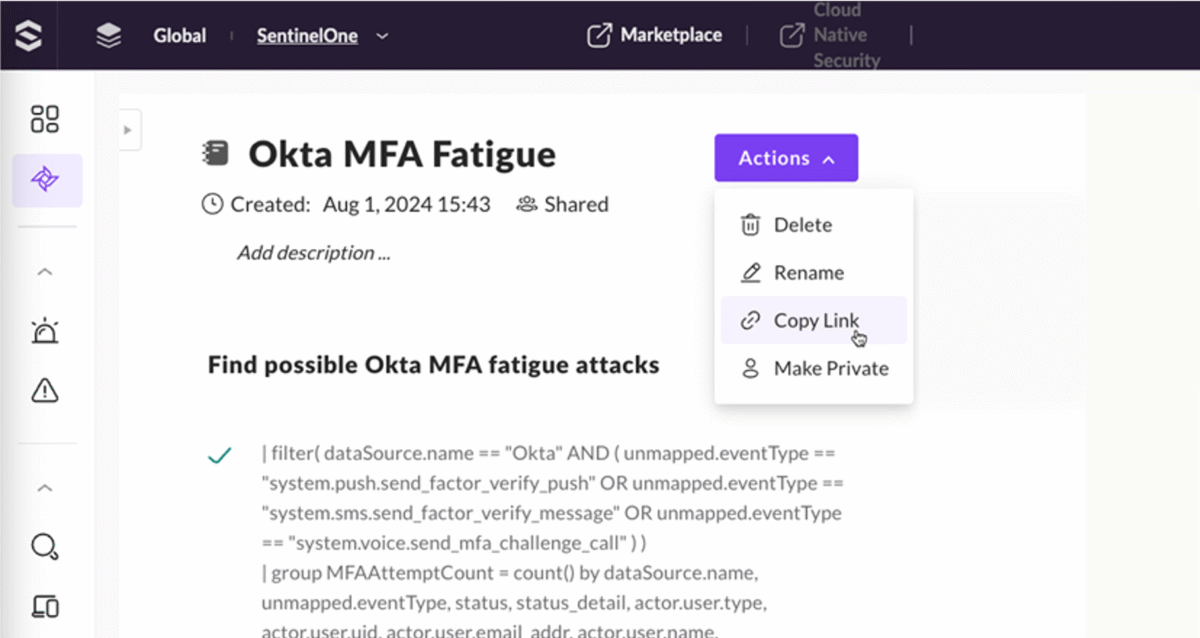
Pinpoint and neutralize cybersecurity risks
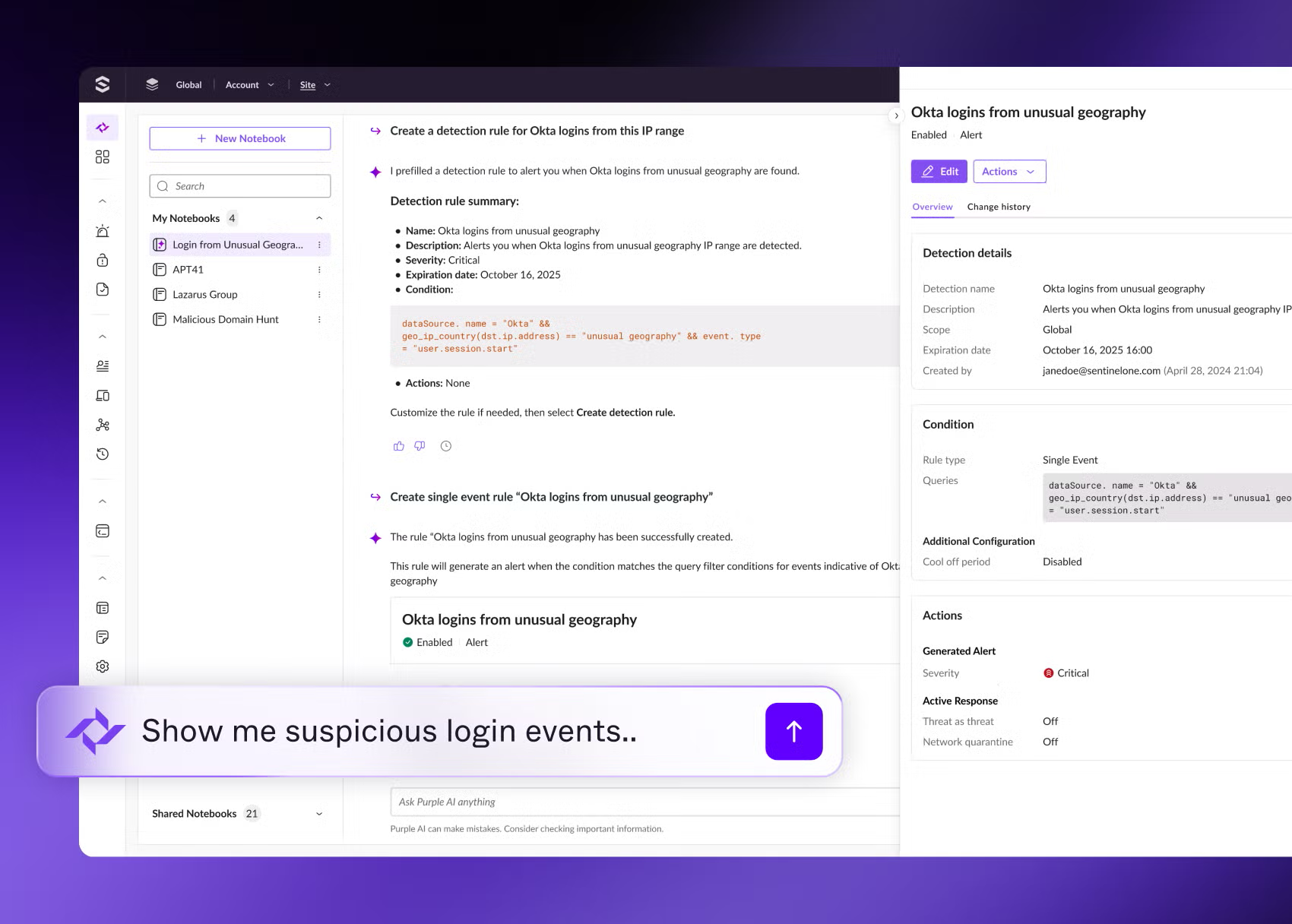
Leverage AI-powered automation to detect, investigate, and respond in real time—reducing impact and preserving business continuity with forensic clarity.
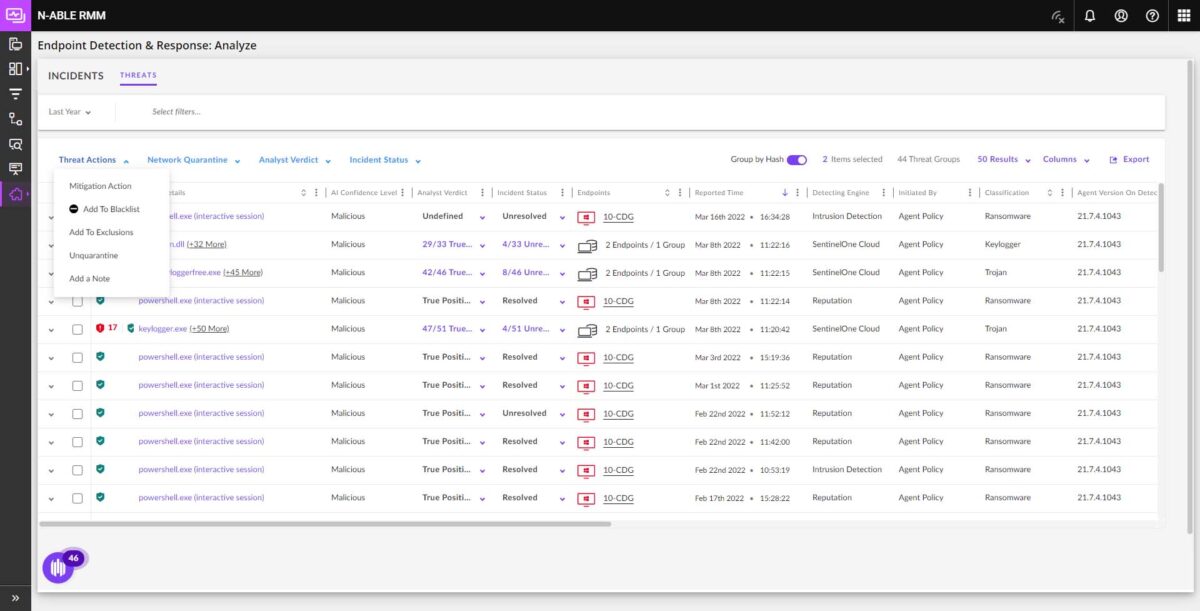
Keep your security stack always safe
Modernize endpoint security with autonomous threat response, deep data retention, and real-time telemetry, ensuring faster recovery and uninterrupted operations.
Why N‑able EDR
Our EDR partner, SentinelOne®, continues to be a Top Performer in the MITRE 2024 Evaluations
Demonstrating an outstanding signal-to-noise ratio. Security teams that can avoid alert fatigue stay ahead of adversaries, rapidly responding to legitimate threats while safeguarding their operations and customers.
For the fifth consecutive year, the Singularity Platform delivered a flawless detection performance, achieving 100% detection at major step level.
Zero detection delays across all simulated attack scenarios.
Scored perfect on detections for attack techniques simulated across Windows, MacOS and Linux systems.
A lot of compliance regulations come from cyber insurance, or different compliances that our customers need to meet. Those forms are filling out and the information they’re asking for—a lot of places are asking for EDR or MDR by name now.
Brad Walser Owner, Walser Technology Group
Tech Solutions deploys N‑able Endpoint Detection and Response (EDR) because with today’s ever-evolving threats, antivirus isn’t enough. EDR can not only stop ransomware in its tracks, it also allows us to roll back to the pre-infected state. We can’t recommend it highly enough to businesses of all sizes.
Scott Beukelman, Network Engineer, Tech Solutions
With multiple AI engines at work, we never have to worry about existing malware, let alone zero-day threats. It’s incredibly easy to deploy, and it can be completely automated. And we can not only protect our customers but show them what happened in an attack with the rich storyline capability.
Dave Brewer, President and CEO, BC Networks
I’ve recently started using EDR. One of the most important features to me is how it can roll back a device if it does detect something malicious, without me even having to touch it. This ticks one of my big fears…an attack could take a long time to fix, and my customer would be down. This is a really, really good feature.
Ken Briscoe, Founder and CEO, Commsit
Visibility, control, and confidence in one place
From deep endpoint telemetry to managed endpoint security services and complete network visibility, these solutions help you respond faster, strengthen compliance, and reduce exposure across your environment.
Threat Hunting
Get deeper visibility into your endpoint data to uncover indicators of compromise.
Attack Surface Management
Achieve full visibility of your network including IoT and BYOD devices without any extra hardware.
Resources
Want to learn more about N‑able EDR?
From ransomware rollback and deep threat visibility to forensic clarity. Explore how N‑able EDR delivers peace of mind.