Resources
This is the place to level up your IT business with an array of force multipliers at your fingertips: live Q&As and demos, pre-written scripts, training, coaching, ready-made marketing, and more.
Filter All Resource Types
Filter All Topics
Filter All Products
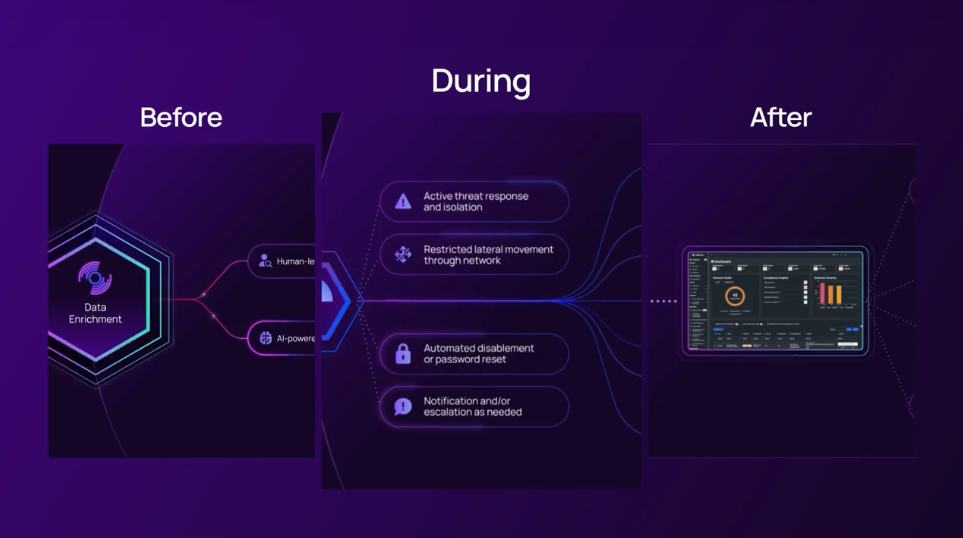
Adlumin: Protection Before, During, and After Cyber Attacks
N‑central Quarterly Roundup – Q4 2025
N‑sight Quarterly Roundup – Q4 2025
Adlumin Quarterly Roundup – Q4 2025
Leading Hotel Group in the Middle East Elevates Cyber Resiliency and Operational Efficiency with N‑able
Cove Data Protection Quarterly Roundup – Q4 2025
This content may contain forward-looking statements regarding future product plans and development efforts. N-able considers various features and functionality prior to any final generally available release. Information regarding future features and functionality is not and should not be interpreted as a commitment from N-able that it will deliver any specific feature or functionality in the future or, if it delivers such feature or functionality, any time frame when that feature or functionality will be delivered. All information is based upon current product
The N‑central Shared Responsibility Matrix
How Fusion Health saves hours each week with N‑central
Clinical Ink’s journey with N‑central
How First Watch Restaurants deployed N‑central in less than one day
SRP Companies’ path to productivity with N‑central
The MDR Value Proposition: Measure Returns on Security Investment
ESG Technical Validation: Cloud-first Backup and Disaster Recovery
A/NZ Webinar – How ThinkConcepts Strengthens Cybersecurity with Adlumin MDR
How First Watch Restaurants Leverage N‑able Solutions to Support 500+ Locations

- Employees: +14,000
- Founded: 1983
- Customer since: 2021
- N-able solutions: N-central, Cove Data Protection
About First Watch
Adlumin MDR meets Halo PSA
Adlumin MDR Demo
N‑central Features for CMMC Compliance
N‑central CMMC Controls Overview
Data Resilience: Best Practices, from Attack Vectors to Remediation
Security Operations and Resilience for the Modern Threat Landscape
Beyond Defense: Accomplishing Endpoint Resilience
The N‑able Vision for End-to-End Cyber Resilience
Security Roundtable: Discussing 5 Key Findings from Our 2025 Threat Report
Preparing for Tomorrow’s Threats Today: The Critical Need for End-to-End Cyber Resilience
EIC transforms global business resilience with N‑able

- Employees: 230+
- Founded: 1975
- Customer since: 2016
- N-able solutions: N-central, Cove Data Protection, EDR, Adlumin MDR, Passportal
About EIC
A/NZ Webinar – AI for MSPs
Committed to helping you meet your CMMC Goals Solutions Brief
Adlumin MDR CMMC Support
The Adlumin Difference Info Sheet
The Ultimate Guide to Malware
The Ultimate Guide to Managing Strong Personalities During a Cyber Crisis
How Intech Hawaii Became the State’s CMMC Compliance Leader

- Employees: 23
- Founded: 1991
- Customer since: 2009
- N-able solutions: N-central, Cove Data Protection, EDR, Adlumin MDR
About Intech Hawaii
Entré Computer Solutions Hits a Home Run with N‑sight

- Employees:
- Founded: 1983
- Customer since: 2012
- N-able solutions: N-sight, Cove Data Protection, EDR, Adlumin MDR
About Entré Computer Solutions
Adlumin Advanced Warranty FAQ
Adlumin Advanced Warranty
From Plan to Practice: Strengthen Incident Response with Tabletop Exercises
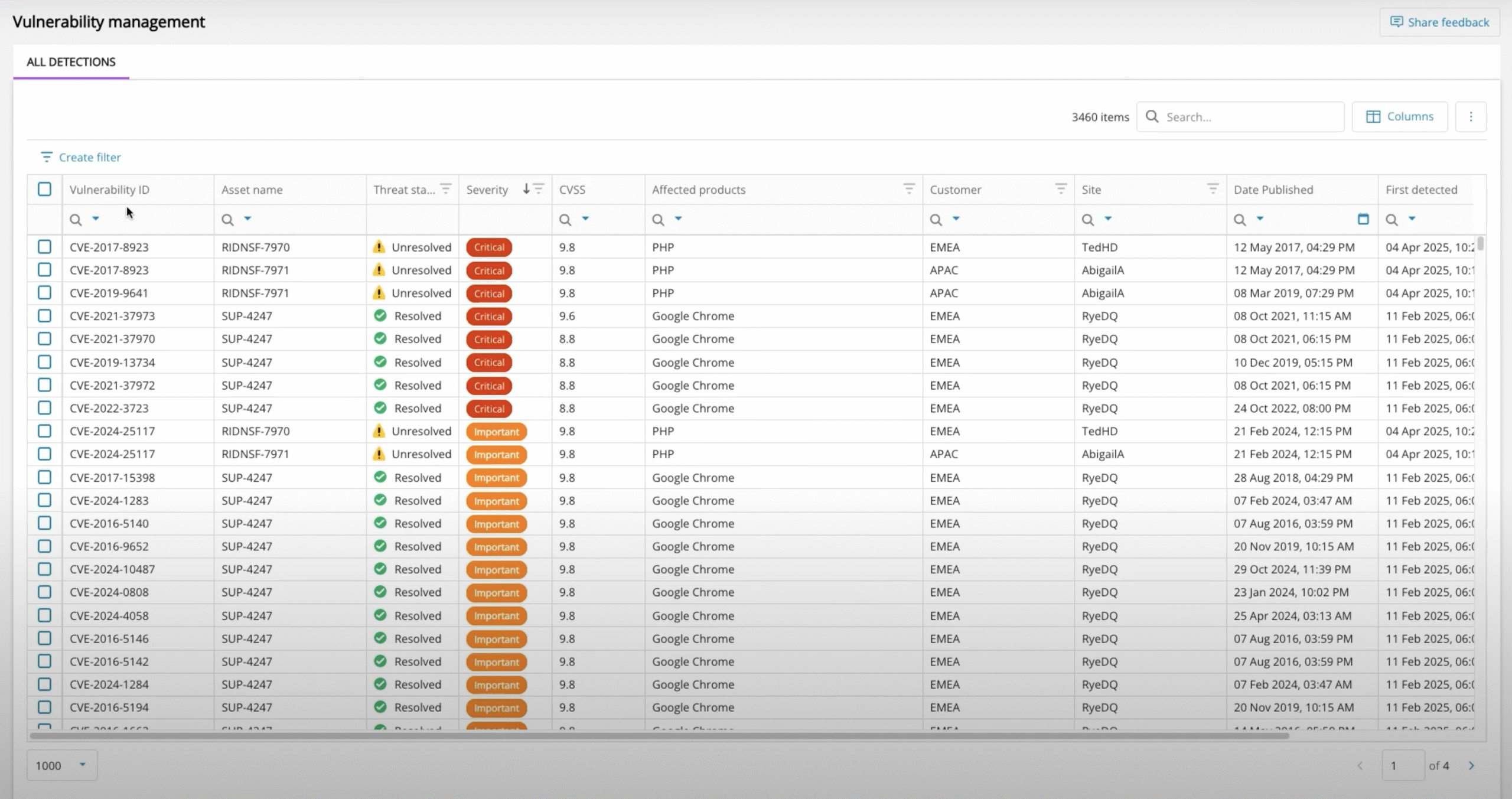
Vulnerability Management Feature Datasheet
N‑able Cyber Resiliency Summit – All Sessions
N‑central Product Onboarding – Infosheet
Cove Data Protection Product Onboarding – Infosheet
N‑central and Your CMMC 2.0 Compliance Journey
With N‑able, CRS Technology Consultants Saves CPA Firm from Business-Crippling Ransomware Attack in Under 24 Hours

- Employees: 10+
- Founded: 1993
- Customer since: 2020
- N-able solutions: N-central, Cove Data Protection, EDR
About CRS Technology Consultants
N‑central Quarterly Roundup – Q3 2025
N‑sight Quarterly Roundup – Q3 2025
Cove Data Protection Quarterly Roundup – Q3 2025
Walser Technology Group Builds a Compliance-First Security Standard

- Employees: 50
- Founded: 2003
- Customer since: 2010
- N-able solutions: EDR, N-central, Cove Data Protection
About Walser Technology Group
N‑central Patch Management Datasheet
N‑able EDR – A Strategic Leap That Doubled Growth for ITC Case Study
- Employees: 100+
- Founded: 2005
- Customer since: 2013
- N-able solutions: EDR
About ITC
MDR Build or Buy
Adlumin Stops Fog Ransomware in Its Tracks
Selecting the Right Solution for Your Organization
Total Ransomware Defense Datasheet
Your Guide to Identity Protection: A Practical Playbook for MSPs
How N‑able technology transformed Walser Technology Group
Threat Blind Spots for MSPs: The 5 Attacks You Can’t Afford to Miss
Protecting Identities Using Adlumin M365 Breach Prevention Masterclass
N‑sight Advantages and Strengths
Inside the Headlines: How Threat Actors Are Exploiting Businesses Like Yours
Building Resilience through Co-Managed MDR/XDR with dotnet

- Employees: 10
- Founded: 2010
- Customer since: 2020
- N-able solutions: Adlumin, EDR, N-central, Take Control, Passportal, Cove Data Protection, DNS Filtering
About dotnet Technologies
Infographic: SMBs Are Now Prime Targets in Cybercrime
Why United Southern Bank of Kentucky Evolved its IT Environment to a Security Operations Platform
How Adlumin Empowers a School District to Secure Over 110,000 Endpoints
Why a Credit Union Protecting $400 Million in Assets Relies on Adlumin’s Managed Detection and Response
Adlumin Provides Total Visibility to Kelly Community Federal Credit Union
How Adlumin’s Progressive Penetration Testing Helped a Financial Institution Immediately Identify Vulnerabilities
Protecting Healthcare Data with Adlumin
Adlumin’s Multi-Tenant Security Platform Delivers Unified Visibility Across 12 School Districts
Utah State Bar Transforms Their Visibility and Compliance Reporting with Adlumin
Media Company Secures Four Million Annual Readers with Automated Cybersecurity
Adlumin Helps a Healthcare Provider Defend Against 250,000 Daily Attacks
Transforming Bank Midwest’s Cybersecurity & Over $1B in Asset Protection
How Ogden City Extended Their Security Operations to 24/7 with Adlumin’s Security Operations Platform plus Managed Detection and Response Services
Scalable Cybersecurity for Maschoff Brennan’s Merger & Acquisition
How Adlumin’s Security Operations Center (SOC) Reduced Government Client’s Notifications by 65%
Adlumin Improves Network Health Score for Financial Plus Credit Union
School District Boosts Security for 19,000 Students and 2,600 Employees with Adlumin
Shedding Light on the Unknown: A Security Operations Platform
Adlumin Contains Cyberattack on a Leading Law Firm in Minutes
The Ransomware Attack That Made MDR Essential – with dotnet Technologies
Adlumin Protect Warranty: FAQs
Adlumin for Education: Safeguarding Learning Environments from Cyber Threats
Adlumin for Financial Institutions: Proactive Cybersecurity for a Complex Threat Landscape
Adlumin for Manufacturing: Securing Smart Industry and the Supply Chain
Adlumin for Municipalities: Defending Public Services Against Modern Cyber Threats
Adlumin for Healthcare: Securing Patient Care and Compliance in a High-Risk Landscape
Adlumin for Law Firms: Defending Confidentiality in a High-Stakes Cyber Landscape
Continuous Vulnerability Management Datasheet
Progressive Penetration Testing Datasheet
Adlumin Incident Response Datasheet
Proactive Security Awareness Datasheet
Executives Overview to Proactive Cybersecurity
The Ultimate Guide to Using Cybersecurity AI
Ultimate Buyer’s Guide to Managed Detection and Response
EDR v XDR v MDR- The Cybersecurity ABCs Explained
Adlumin Security Posture Program Guide
Adlumin Packaging Guide
Adlumin Protect Warranty
Cove Data Protection Quarterly Roundup – Q2 2025
N‑sight Quarterly Roundup – Q2 2025
N‑central Quarterly Roundup – Q2 2025
Staying Data-Resilient for Cyber Insurance
Lemontree chose N‑central to drive customer satisfaction and managed services excellence

- Employees: 75
- Founded: 1998
- Customer since: 2011
- N-able solutions: N-central
About Lemontree
Cyberattacks in Healthcare: The Stats Behind the Need for Cloud-Native Data Protection
Three Reasons Cloud-Native Data Protection is Vital in Healthcare
Threat Response and Investigation: What to Do From Alert to Action
N‑central Quick Overview
The IT Leader’s Playbook for Smarter Automation
Unleashing Protective DNS: The First Line of Cyber Defense You’re Still Underestimating
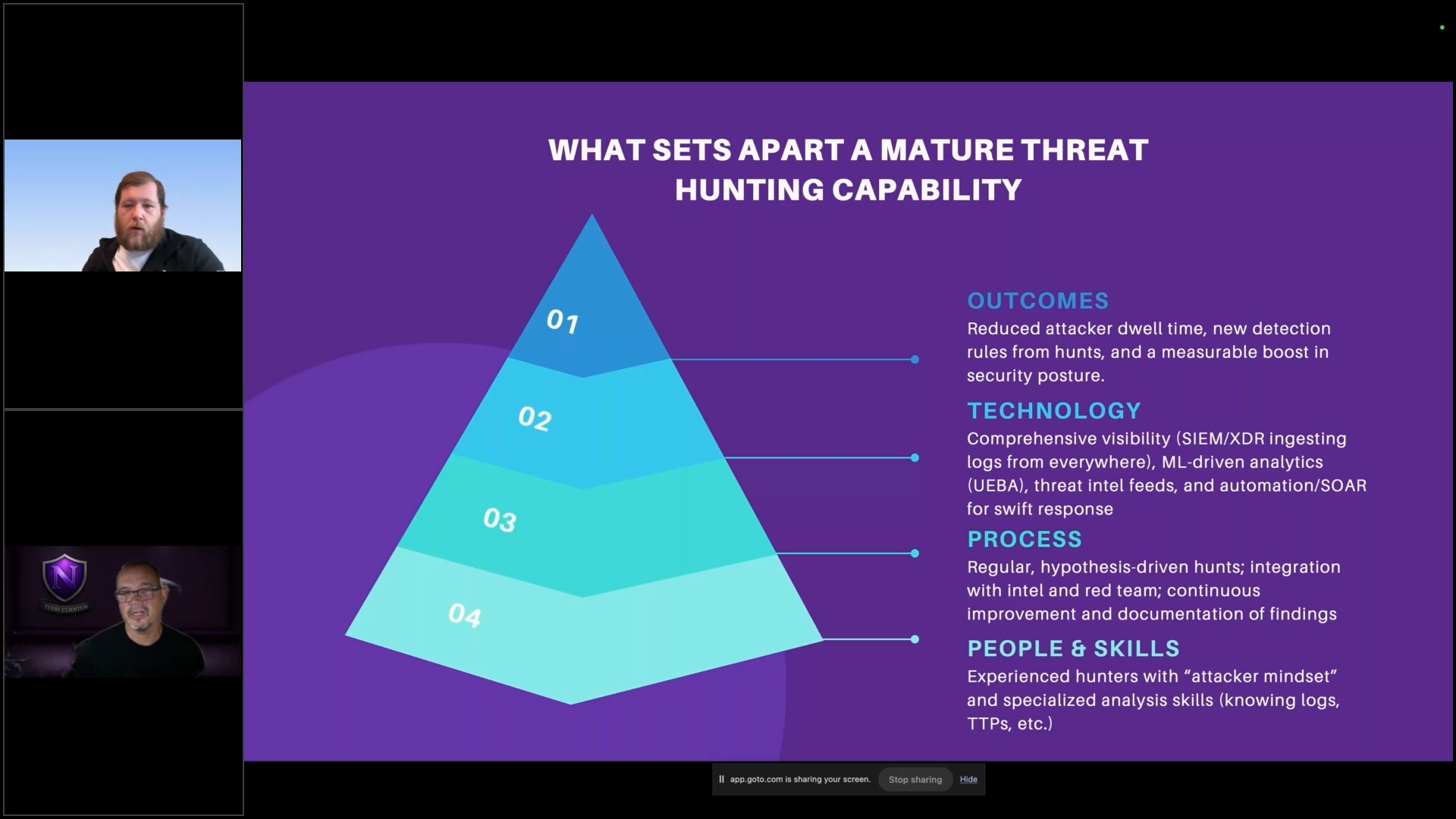
Threat Hunting Explained: See It in Action, Learn How It Works
IT & Security Operations Convergence Project Template
ITOps and SecOps Tech Stack Checklist
ITOps and SecOps Internal Audit
N‑able EDR – A Strategic Leap That Doubled Growth for ITC
N‑able EDR (powered by SentinelOne) Feature Comparison Sheet
How to Innovate with AI: A Practical Guide for SMEs and Enterprises
How to Use Security Integrations to Support Regulatory Compliance
Unifying ITOps and SecOps
Towards Resiliency – First Secure’s Cybersecurity Evolution

- Employees: 150
- Founded: 1985
- Customer since: 2024
- N-able solutions: Endpoint Detection and Response , Adlumin Security Operations
About First Secure
The Guide to Using Cybersecurity AI
Canalys Managed BDR Leadership Matrix 2025
Why choose to resell N‑central UEM?
Outdated Backup Holding You Back? This Playbook Shows How to Fix It
CMMC: A guide to the What, When, Why, and How?
Understanding MFA Bypass Techniques and EvilGinx 3: A Guide for IT Professionals
How to Choose an MDR Provider: A Guide for IT Professionals
How to Use Network Visibility in Your Cyber Security Strategy
2025 State of the SOC Report: The Impact of AI on SOC Services
SOC Success: See the Risks, Stop the Breach, Prove the Value
Reseller Partner Program benefits
Why Re-sell N‑able Security Solutions?
Cove Data Protection Quarterly Roundup – Q1 2025
Quarterly Roundup Q1 2025 N‑central
Quarterly Roundup Q1 2025 N‑sight
How to Use Security Integrations to Support Regulatory Compliance
MidSolv Case Study: Overcome Ransomware and Strengthen Cybersecurity with N‑able MDR and Cove
Adlumin Identity Threat Detection and Response
N‑able Vulnerability Management Demo – Now in Preview
State of the SOC Report – 2025
SOC Success: See the Risks, Stop the Breach, Prove the Value
The importance of data efficiency in optimizing cyber resilience and data protection
Preventing a Cyber Attack Against the CEO of Real IT Care, a Healthcare Organization

- Employees: 300
- Founded: 2009
- Customer since: 2024
- N-able solutions: Adlumin Security Operations
About Real IT Care
Why re-sell Cove Data Protection over competitors?
How to Use Network Visibility in Your Cyber Security Strategy
MSP Horizons Report 2025
MSP Horizons Report 2025 Infographic
Cybersecurity Incident Response Plan
MDR Fireside Chat: How MDR keeps MSPs protected
Watch an EvilGinx Demonstration to See How Cybercriminals Bypass MFA
Cove Data Protection Quarterly Roundup – Q4 2024
N‑sight Quarterly Roundup – Q4 2024
MDR Compliance Data Sheet
N‑central Quarterly Roundup – Q4 2024
Key Features of Adlumin XDR Platform
Merger & Acquisition considerations for your MSP business
Joint Adlumin and N‑able Demo- Strengthen your cybersecurity arsenal with XDR and MDR
Fireside Chat: NIS2’s Impact on MSPS
The most significant cyber updates in the EU – The NIS2
NIS2 can grow your MSP. Here’s how.
How to comply with NIS2?
What does NIS2 mean for MSPs?
5 Quick and Easy Things that you Should be Automating with N‑sight
N‑central Automation Masterclass
MSPs on the Frontline
Dealing with an event: Adlumin MDR Makes a Huge Difference
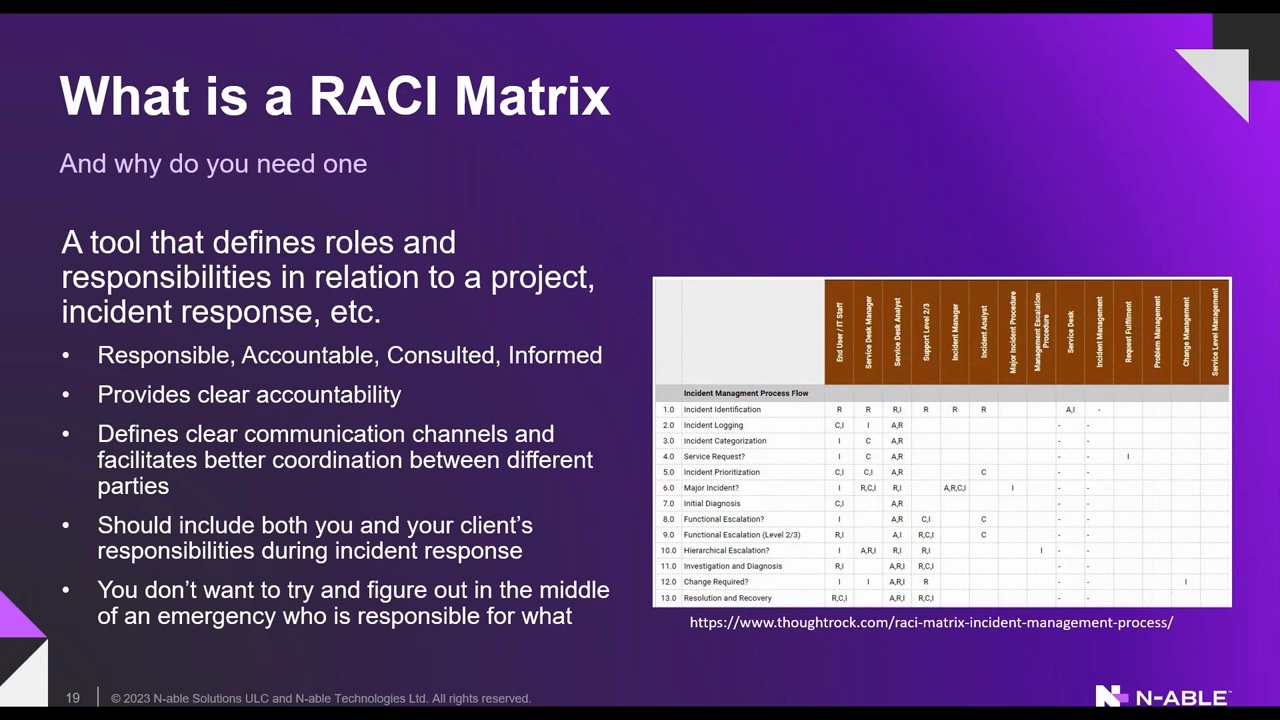
RACI Matrix for Compliance, Risk Management and a Robust Cyber Security Posture
What Types of Coverage Do My Business and My Customers Need?
Adlumin MDR helps Ventnor City prevent a ransomware attack within 6 hours of deployment

- Employees:
- Founded: 1903
- Customer since:
- N-able solutions: Adlumin Security Operations, N-sight RMM, Cove Data Protection, Endpoint Detection and Response, Mail Assure, Passportal, Take Control
About Ventnor City
What is First-party Cyber Liability Insurance?
What is Third-party Cyber Liability Insurance?
What is cyber liability insurance?
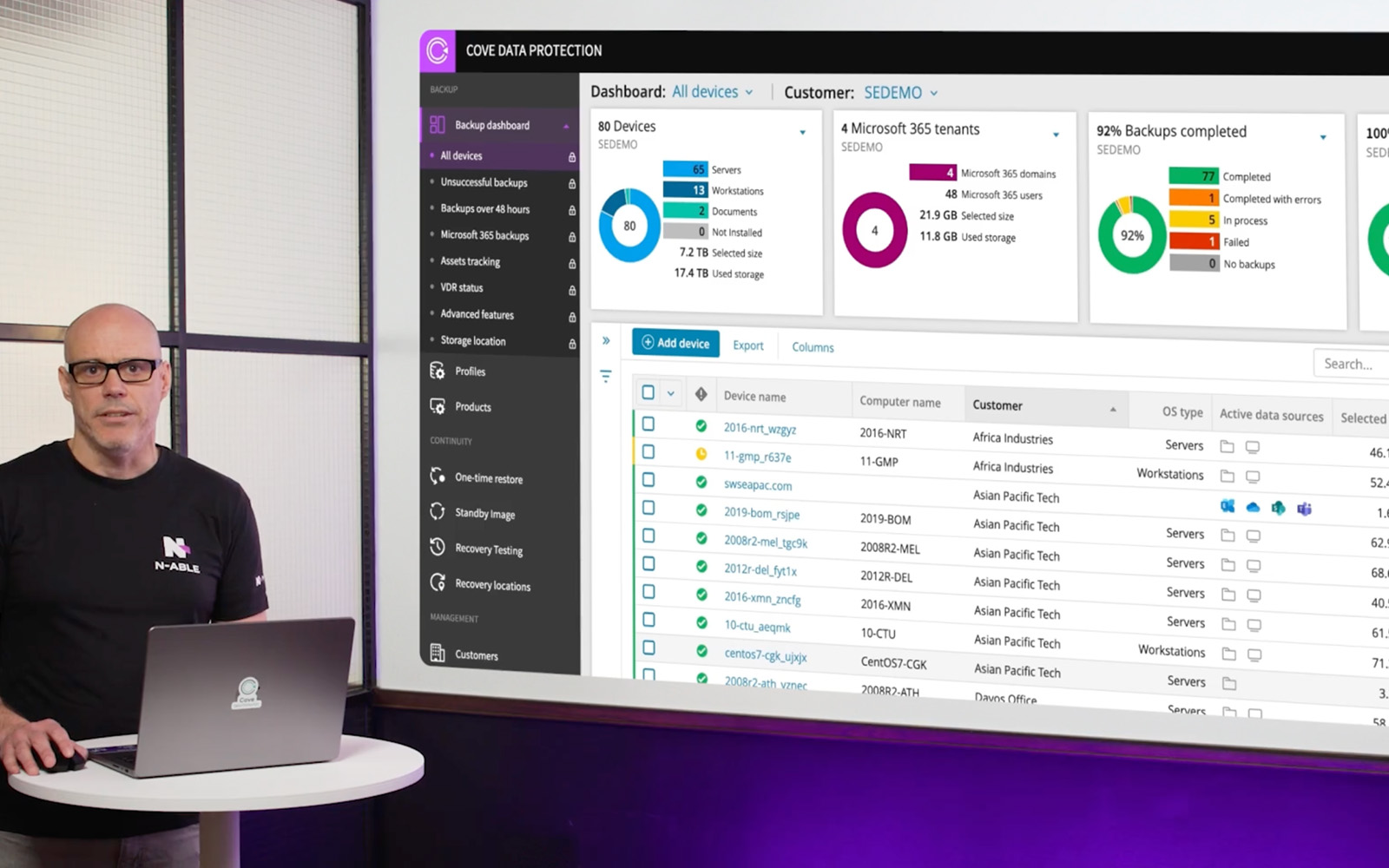
N‑able Cove Data Protection™ Q3 Quarterly Roundup
N‑able N‑central™ Q3 Quarterly Roundup
N‑able N‑sight™ Q3 Quarterly Roundup
N‑able N‑sight helps Informatica Ros expand their boundaries

- Employees: 9
- Founded: 1998
- Customer since: 2024
- N-able solutions: N-sight RMM , Cove Data Protection , Endpoint Detection and Response
About Informatica Ros
Utilize Ltd., UK-based leading MSP Ditches Legacy BDR for Cove
NIS2 Directive: What it Means for Managed Services Providers
Cove Data Protection Update – Oct 2024
Analysis of NIS2 and Expected Impact on Managed Service Providers (MSPs) and Managed Security Service Providers (MSSPs)
5 Reasons You Need Cove Data Protection
How to Choose an MDR Provider. Five Questions You Need to Ask
From Breakfix to MSP Lesson 2
Cisco Umbrella EOL Direct
N‑hanced Services Feature Sheet
N‑hanced Services Working with Premium Support
Cove Data Protection Update – August 2024
What is the MITRE ATT&CK Report and Why is it Important to You?
15 Minutes to Cyber Insurance-Ready Backups
Defend & Prosper – Maximizing the Cybersecurity Opportunity
How Infoprotect Places N‑sight at the Centre of Their Cybersecurity Offering
How N‑able Helped PSD Net Revolutionize the Way They Work

- Employees:
- Founded: 2002
- Customer since: 2009
- N-able solutions: N-central, Cove Data Protection, Passportal
About PSD Net
Cove Data Protection: Back up Microsoft 365, easy as 1-2-3
Cove Data Protection: Flexible Disaster Recovery Made Simple
Cove Data Protection™ for Microsoft 365 For Internal IT
Cloud-first Data Protection as a Service
EDR Threat Hunting Feature Sheet
How to price an advanced security program
How to price an essential security program
Top ways to handle the risk conversation for MSPs
MSP pricing mistakes and how you can fix them
How does pricing work with MSPs?
Cove + Microsoft: Unlock new revenue and faster recovery
Cove Data Protection: Cyber Resilience
N‑able Ecoverse Explained
Cove Data Protection Update – June 2024
Cove Data Protection Update – May 2024
Busy Township IT Team Relies on Cove Data Protection

- Employees: 350
- Founded: 1745
- Customer since: 2023
- N-able solutions: Cove Data Protection , N-central , MSP Manager
About Franklin Township
The MSP’s Guide to Winning with Sales and Marketing
How Broadcom’s VMware pricing changes in 2024 forced one company to evaluate their options
How to Use Security as a Catalyst to Drive Revenue
AI for MSPs
Adlumin Managed Detection and Response Ransomware Prevention
Unlock Profitability with Cove Data Protection
The N‑able Advantage
How N‑able Transformed Comfox’s Data Protection

- Employees: 22
- Founded: 2010
- Customer since: 2016
- N-able solutions: Cove Data Protection , N-sight RMM
About Comfox
Cove Data Protection Update – April 2024
Defending against the now and the next in cyberthreats
RemoteOps Forensics Feature Sheet
N‑sight Helps Ready Digital Dive Deeper Into Its Customers’ Networks

- Employees: 50
- Founded: 1981
- Customer since: 2011
- N-able solutions: N-sight RMM, Cove Data Protection
About Ready Digital
Cove Data Protection Update – March 2024
Cove Data Protection Update – February 2024
Security Reinvented: Omega Systems’ Transformation with Adlumin MDR
- Employees:
- Founded:
- Customer since:
- N-able solutions: Adlumin MDR
About Omega Systems
Unveiling Adlumin MDR: The Peer-to-Peer Webinar
N‑sight Helps One Team Deliver a Support Service Made for Today’s Market

- Employees: 80
- Founded: 1997
- Customer since: 2019
- N-able solutions: N-sight RMM, Cove Data Protection
About One Team
N‑able N‑sight RMM Update – February 2024
N‑able N‑sight RMM Update – March 2024
WW Works Chooses Cove for Efficient, Reliable Backup and Predictable Costs

- Employees: 10
- Founded: 1990
- Customer since: 2015
- N-able solutions: Cove Data Protection
About WW Works
From Breakfix to Managed Service Provider
MSP Horizons Report at a Glance
Critical Insights for MSPs in 2024
Key Features of Adlumin MDR
Five Apple Management Myths
Integrating Endpoint Detection and Response for N‑central
The MSP Horizons Report – 2024
Introducing MDR
XDR versus MDR
Darknet Exposure Monitoring
One Education Ltd Transforms Service with Cove Data Protection

- Employees: 230
- Founded: 2011
- Customer since: 2018
- N-able solutions: Cove Data Protection, N-sight RMM, Take Control, Mail Assure, MSP Manager
About One Education Ltd
Getting started with EDR in N‑central
Canalys BDR Leadership Matrix 2023
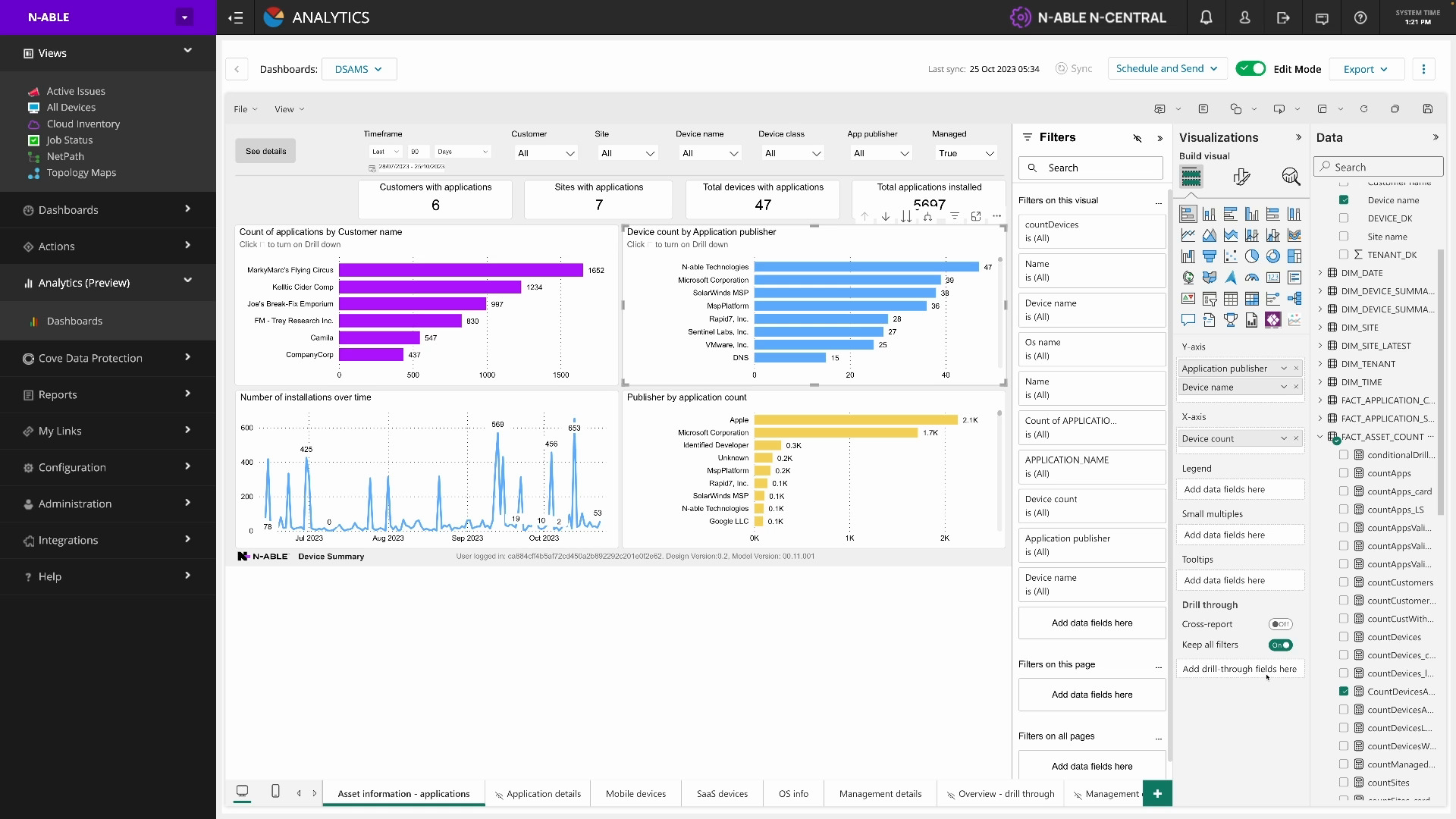
N‑central Analytics Demo
N‑able EDR: Attack Surface Management FAQ
Co-Managed Digital Playbook
Apple Device Management with N‑central
EDR N‑central Data Sheet
N‑central Analytics Overview
Managing Apple Devices in N‑central
N‑sight helps Out of a Jam Solutions manage their Apple devices efficiently and effortlessly

- Employees: 7
- Founded: 2000
- Customer since: 2016
- N-able solutions: N-sight RMM, Cove Data Protection
About Out of a Jam Solutions
Get to know N‑central
Why WeCybers partners with N‑able
Kick ICT Group stands by Cove Data Protection
5 challenges MSPs face when selling security programs
APAC – All Partners Meeting Including N‑central & Security Roadmaps
APAC – All Partners Meeting Including N‑sight & Security Roadmaps
Leveraging Cybersecurity Frameworks to Drive Business Growth
Get to know Cove Data Protection
Get to know Cove Data Protection
Attack Surface Management Data Sheet
N‑sight Product Tour – MSPs love N‑sight. See how it can help you too
N‑sight Product Tour – What is N‑sight and why are MSPs raving about it?
N‑sight Product Tour – Cover all devices and operating systems with N‑sight
N‑sight Product Tour – Why N‑sight works perfectly with Apple devices
N‑sight Product Tour – Automate, monitor, and manage devices at scale with N‑sight
N‑sight Product Tour – How N‑sight made remote access to your partners easier
N‑sight Product Tour – A ticketing solution already integrated in an RMM?
N‑sight Product Tour – How N‑sight gets MSP reporting right
N‑sight Product Tour – The RMM security solution that protects customers long term
N‑sight Product Tour – Is your RMM helping you succeed? See how N‑sight can
N‑sight Product Tour – How N‑sight’s pricing is based on business growth
N‑sight Product Tour – How to get N‑sight set up on your devices
N‑hanced Services Offerings Overview
2023-2024 DCIG Top Five – Cove Data Protection for Microsoft 365
How to get the best out of Patch Management on N‑sight RMM
Reliable Networks Standardizes Application Stack with N‑able Products

- Employees: 35
- Founded: 2004
- Customer since: 2022
- N-able solutions: N-central, Cove Data Protection, EDR, Passportal
About Reliable Networks
How can EDR help you? Gary Saunders of Form IT Solutions explains
A co-founder’s thoughts on selling security and the impact of N‑able Roadshows
AV or EDR? How one director’s decision benefited his business
Why the experienced managing director of Aonix upgraded to N‑able EDR
Case Study: Compass Technology Managers Gets More Proactive with N‑able N‑sight
N‑able N‑sight RMM For IT Pros
N‑sight allows Mnemonica to save time and resources
Southridge Technology: Reaping the Rewards of a Long-term Relationship
Unlocking your IT possibilities with N‑sight RMM Bundle
How to Know When Your MSP Has Outgrown Your RMM Tool
Cove Recovery FAQ
StarNet Keeps Customers Happy with N‑able Solutions

- Employees: 15
- Founded: 2001
- Customer since:
- N-able solutions: N-central, Cove Data Protection, Mail Assure, N-sight
About StarNet
DNS Filtering Standalone Infographic
DNS Filtering Standalone Feature Sheet
N‑able Reseller Program
N‑sight: What is Included
Connecting Point – 20 Years of Partnership and Growth as a Family-Run MSP
Omega Systems saved time and resources with N‑central
N‑central Allows Accurate Networks to Proactively Manage Customer Environments

- Employees: 33
- Founded: 2024
- Customer since:
- N-able solutions: N-central
About Accurate Networks
Managing Apple Devices in N‑sight – Getting Started Guide
ESG Technical Validation: Cloud-first Backup and Disaster Recovery
N‑sight gives Consulea everything they need as an MSP

- Employees: 10
- Founded:
- Customer since:
- N-able solutions: N-sight RMM
About Consulea
Add experts, not expense, with N‑able Managed EDR
N‑able Layered Security for Managed Service Providers
EDR N‑sight Datasheet
Managed Services Pricing Guide 4.0: Industry Best Practices (ASD)
Managed Services Pricing Guide 4.0: Industry Best Practices (CAD)
Managed Services Pricing Guide 4.0: Industry Best Practices (EUR)
Managed Services Pricing Guide 4.0: Industry Best Practices (USD)
Endpoint Detection and Response Demystified
AV to EDR: What You Need to Know
The Case for Managed SOC Services: A Quick ROI Guide
SOHO Solutions provides best-inclass data protection with Cove

- Employees: 15
- Founded: 1997
- Customer since:
- N-able solutions: Cove Data Protection, N-central
About SOHO Solutions
Master-Hardware Kft. on why choosing N‑able through Biztributor made their everyday business life easier
N‑hanced Services: A Closer Look
Cove Data Protection for Microsoft 365 Supports Escalon Services’ Strong Security Backbone

- Employees: 1200
- Founded: 2008
- Customer since:
- N-able solutions: Cove Data Protection
About Escalon Services
ComTec Solutions Empowers Customers Using N‑central to Manage Their Infrastructures
Scaling backup through Exbabylon IT’s customer base with Cove
CEO of Oxygen Technologies explains how Cove exceeded his expectations
Fortress SRM Ensures Risks are Mitigated Using the N‑central Platform

- Employees: 200
- Founded: 2021
- Customer since:
- N-able solutions: N-central
About Fortress SRM
Managed Endpoint Detection and Response Datasheet
Eight Reasons to Back Up Microsoft 365 Data
N‑central by the numbers Infographic
Passportal Product Roadmap
MSP Manager Product Roadmap
Take Control Product Roadmap
Cove Data Protection Product Roadmap
N‑central RMM Product Roadmap
Thanks to N‑able we can provide SMBs with enterprise technologies
I am relieved to take care of data protection in a minimalist way
Endpoint Detection and Response: How to Demonstrate ROI
Cove Continuity Feature Sheet
Ransomware Missteps that Can Cost You
N‑sight Product Roadmap
What type of disaster are you facing?
N‑central Advantages and Strengths
Automation Manager: A feature available with N‑able N‑central
N‑central: 10 things to look for in an RMM solution
N‑able EDR and SentinelOne deliver for Ballast Services
N‑able N‑hanced (Technical) Services – Getting Started Guide
Easy Solution MSP chose N‑able EDR for today’s complex cybersecurity landscape
Patch Management for IT Pros: A feature available with N‑able N‑sight RMM
Automation Manager: A feature available with N‑able N‑sight RMM
N‑able N‑sight RMM: Unlocking IT possibilities for the future
Managed Antivirus: A feature available with N‑able N‑sight RMM
10 things to look for in an RMM solution
N‑sight RMM Mac Device Management for IT Pros
Endpoint Detection and Response Standalone Datasheet
Threat Hunting: An advanced feature of N‑able EDR
How to Develop a Successful Threat Hunting Program
MITRE Engenuity ATT&CK evaluation
Rethink Backup IT Pro Infographic
Mail Assure Billing FAQ
Ransomware Recovery FAQ
N‑hanced Technical Services Catalogue
The Big Book of Data Protection ROI
More for Your Money With the Cove Data Protection Plan
Cove Data Protection IT Pro
Cove for Microsoft 365
Cove Data Protection Datasheet
Cove Data Protection support: if It’s critical to you, it’s critical to us
Cove Data Protection Documents
Cove Data Protection Worldwide Data Centers Designed for Security
N‑able Devices Layer Focus Sheet
N‑hanced Services – Technical Services
N‑able N‑hanced Services – Custom Solutions
N‑able N‑hanced Services – Onboarding
N‑able N‑hanced Services – Support
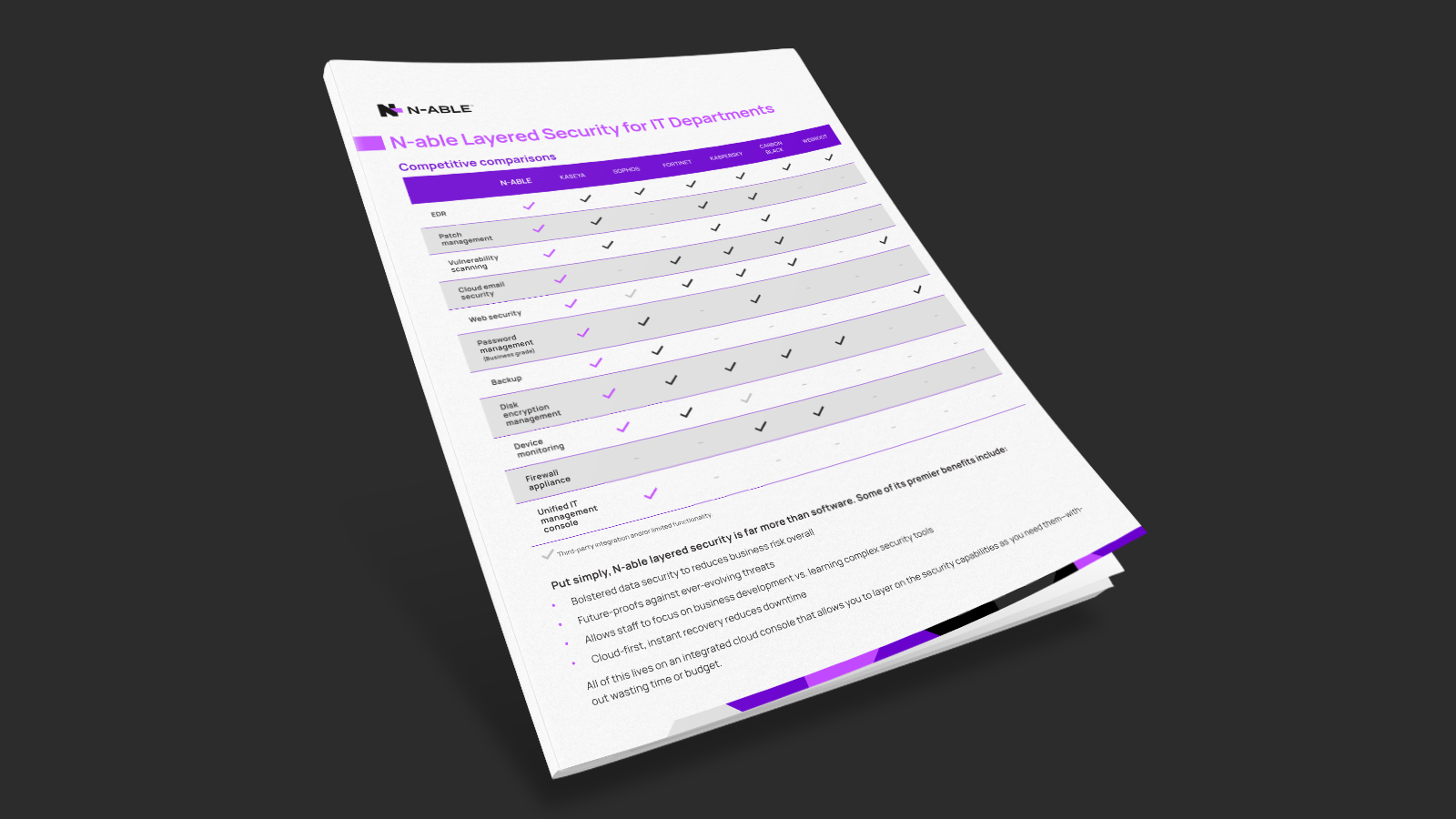
N‑able RMM Layered Security for IT Departments
N‑able Application Layer Focus Sheet
Mail Assure Private Portal
Mail Assure Private Portal FAQ
N‑able Layered Security Comparison for IT Departments
The New Threat Landscape: Pushing MSP Security to the Next Level
Managed Services Pricing Guide 4.0 (UK)
N‑central and What Is Included
State of the Market: The New Threat Landscape
Web Filtering Technologies: Which type of filtering will keep me most secure?
Configuration, Filtering Policies, and Reporting
Worldwide Data Centers: Reliable, scalable, fast
Threat Protection: What kind of threats does N‑able DNS Filtering protect my customers against?
Why Email Security Matters
RMM EDR vs. AV: What You Need to Know
Antivirus vs. EDR: at a glance
Stack the Security Deck in Your Favor
Passportal Site Datasheet for IT Pros
7 Business Advantages of Being an N‑able Partner
Passportal Blink Datasheet
The Frightening Facts of Email Attacks Infographic
Technologies of Trust: Protecting Against Email Fraud and Scams Infographic
Using Documentation to Boost MSP Efficiency and Drive Profitability Whitepaper
Rogers Insurance Uses N‑central to Handle Rapid Change Case Study
Passportal Site Data Sheet
RMM and PSA integration Infographic
Automation Secrets for Effortless Endpoint Management
N‑able EDR Rollback: A Cybersecurity Time Machine eBook
How do you save your passwords?
Keeping your customers secure while they work from home
Take Control: Built for Secure Remote Access eBook
Take Control Plus Data Sheet
The Big Book of Selling Data Protection
The Right Fit: Winning Customers by Finding the Right Program Fit eBook
Passportal Documentation Manager Data Sheet
Networks These Days: Boosting Network Visibility in Complex Environments Whitepaper
N‑able helped InfraNet Solutions build a safe haven for their clients
Passportal Automated Workflows Feature Sheet
Integrating Your RMM and PSA Tool: Your Path to Proactive Managed Services eBook
Anywhere Protection: The New State of Cybersecurity Infographic
DNS Filtering Feature Sheet
Traction IT on recovery with N‑able Backup
Traction IT on the impact of N‑able Backup on their staff
Traction IT on N‑able Backup’s benefit to customers
Traction IT – The impact for an MSP owner and profitability
Traction IT on discovering N‑able Backup
Traction IT – Taking a second look at Veeam
N‑able Mail Assure
RMM Mobile Device Management Feature Sheet
The Big Book of Layered Security eBook
N‑able N‑central + Microsoft Intune Feature Sheet
Layered Security: Essential for Protecting Business Growth Infographic
Rethink Backup Infographic
Ransomware Rescue: How to Recognize and Avoid a Data Hostage Situation Infographic
N‑sight and MarketBuilder helped C&W Technologies grow their business
The State of Layered Security in 2021 Infographic
5 Best Practices for Onboarding New Customers eBook
N‑able Passportal | Centralized IT Documentation for MSP Efficiency
N‑central Security Manager – AV Defender Feature Sheet
Six Months Later: Secrets of Choosing RMM Tools That Last eBook
Protect Business Growth with Cybersecurity Info Sheet
Why You Should Move from Service Desk to MSP Manager Info Sheet
MSP Q&A: Bart Zub, Digimite Technology
Technology Alliance Program Overview Info Sheet
Technology Alliance Program: How to Get Started with N‑central Guide
Technology Alliance Program: How to Get Started with RMM Guide
Getting Started with Endpoint Detection and Response Guide
How to Use Your Remote Access Account Guide
How to Get Started with N‑able Take Control Guide
Passportal + Documentation Manager Quick Start Guide for MSPs
Take Control gave Pelycon Technologies the ability to offer instant IT support
Getting Started with N‑able Passportal + Documentation Manager Guide
9 Reasons to Use N‑able Mail Assure Info Sheet
4 Password Risks and How to Handle Them eBook
Resilient Business Systems and its customers enjoy the benefits of the N‑able Take Control solution
PCnet uses N‑able EDR because it gives their customers peace of mind
RMM Automation Manager for IT Pros Feature Sheet
Keep Your Customers Safe on Microsoft 365 Infographic
Is Email Putting Your Business at Risk? Infographic
Passportal data protection in transit and at rest
N‑central Disk Encryption Manager
N‑central Network Device Monitoring
N‑able N‑central Network Topology Mapping
N‑central for IT Pros
Mail Assure Data Sheet
RMM Managed Antivirus Feature Sheet
Five Ways Great MSPs Automate Their Businesses eBook
5 Tips for Preventing Harm After an Employee Leaves Infographic
N‑central Unified Endpoint Management Datasheet
Protecting Microsoft 365 with Mail Assure
Five Cyberthreats Managed Service Providers and IT Professionals Can’t Ignore in 2026
Apple Device Management with N‑sight
RMM Patch Management Feature Sheet
RMM Disk Encryption Manager Feature Sheet
RMM Web Protection Feature Sheet
N‑able MSP Manager: Integrated with N‑able N‑sight RMM
SpamExperts Incoming Email Filter Data Sheet
SpamExperts Outgoing Email Filter Data Sheet
SpamExperts Email Archiving Data Sheet
Mail Assure Advanced Email Security for Microsoft 365 Feature Sheet
N‑central PSA Integration Feature Sheet
Take Control and Passportal Integration
Passportal Blink
N‑able Take Control Data Sheet
Mail Assure Microsoft 365 FAQ
N‑able Take Control vs. Take Control Plus: What’s Right for Your Business?
N‑central + Microsoft Intune FAQ for MSP Partners
Nothing to display

If you’re in IT, the Head Nerds have your back. These experts offer guidance, solutions, and strategies with real human connection, through live Boot Camps, regular Office Hours, and insightful blog posts.

More helpful resources from N‑able
Upcoming events
Office Hours: Cove Data Protection
January 20 2026, 11:00 - 12:00 EST (17:00 - 18:00 CET)
Become a Master of Ransomware Response – January
January 20 2026, 11:00 - 12:00 EST (17:00 - 18:00 CET)
A/NZ Webinar: Backup & DR at Scale – Overcoming Complexity and Cyber Risk
January 21 2026, 11:30 - 12:30 AEDT (19:30 - 20:30 EST)
January 27 2026, 10:00 - 11:00 EST (16:00 - 17:00 CET)
Network Buying Group – Vision 2026
January 28 - January 29 2026
Office Hours: Adlumin MDR
January 28 2026, 11:00 - 12:00 EST (17:00 - 18:00 CET)
January 29 2026, 11:00 - 12:00 EST (17:00 - 18:00 CET)
Right of Boom 2026
February 3 - February 6 2026
February 3 2026, 11:00 - 12:00 EST (17:00 - 18:00 CET)
MSP Expo
February 10 - February 12 2026
Latest blog posts
RTO vs RPO: How Are They Different?

By N‑able
January 18th, 2026 11 min read
Data Protection in the Cloud: How to Get It Right

By N‑able
January 17th, 2026 13 min read
8 Real-World Cyber Resilience Examples

By N‑able
January 15th, 2026 13 min read

By N‑able
January 14th, 2026 5 min read
From Compliance Burden to Business Boomer: Navigating CMMC with Confidence

By N‑able
January 13th, 2026 6 min read
Enterprise Patch Management Best Practices: The Complete Guide

By N‑able
January 13th, 2026 14 min read

By N‑able
January 8th, 2026 7 min read

By N‑able
December 31st, 2025 16 min read
How to Build a Cyber Resilience Strategy in 10 Steps

By N‑able
December 29th, 2025 11 min read

By N‑able
December 23rd, 2025 11 min read